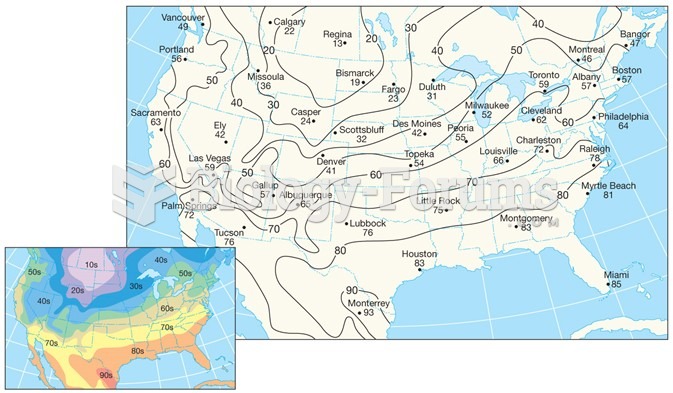
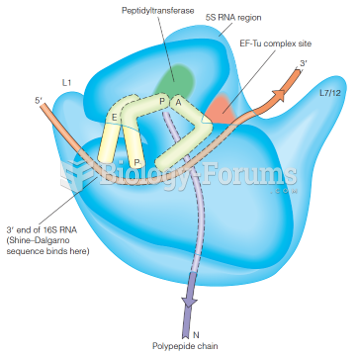
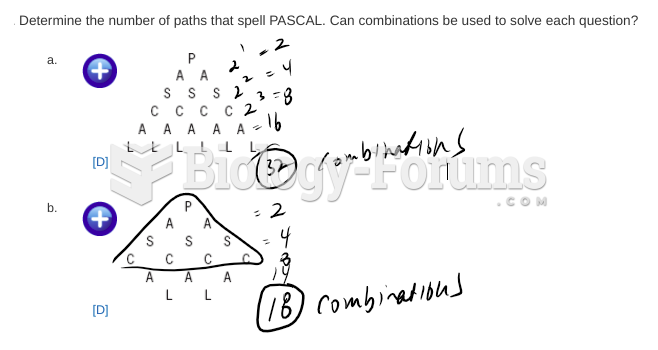
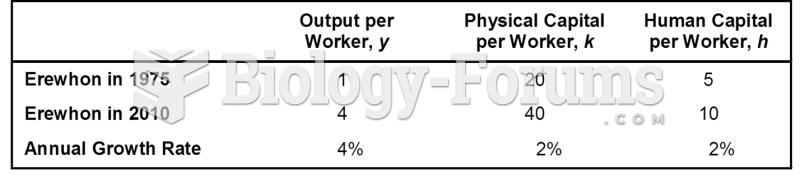|
|
|
Only one in 10 cancer deaths is caused by the primary tumor. The vast majority of cancer mortality is caused by cells breaking away from the main tumor and metastasizing to other parts of the body, such as the brain, bones, or liver.
Earwax has antimicrobial properties that reduce the viability of bacteria and fungus in the human ear.
Calcitonin is a naturally occurring hormone. In women who are at least 5 years beyond menopause, it slows bone loss and increases spinal bone density.
A recent study has found that following a diet rich in berries may slow down the aging process of the brain. This diet apparently helps to keep dopamine levels much higher than are seen in normal individuals who do not eat berries as a regular part of their diet as they enter their later years.
When blood is exposed to air, it clots. Heparin allows the blood to come in direct contact with air without clotting.