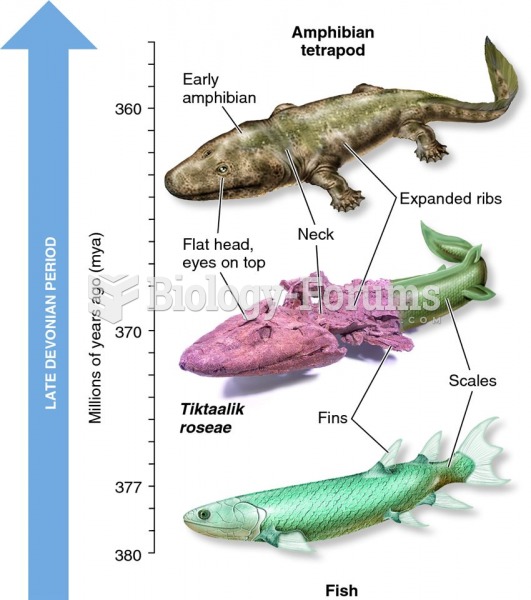
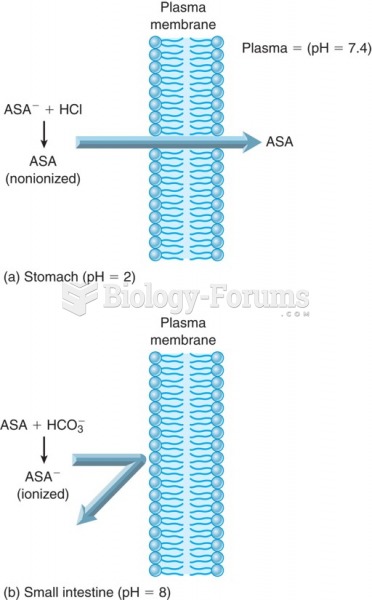
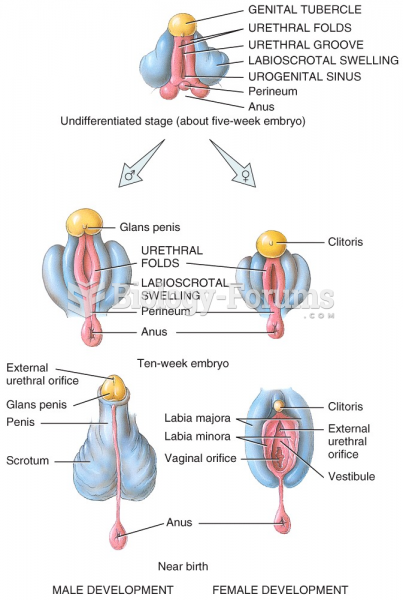
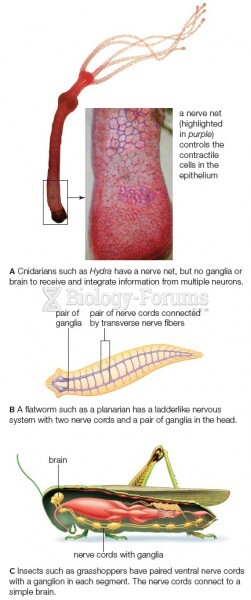
|
|
|
The people with the highest levels of LDL are Mexican American males and non-Hispanic black females.
Drying your hands with a paper towel will reduce the bacterial count on your hands by 45–60%.
For about 100 years, scientists thought that peptic ulcers were caused by stress, spicy food, and alcohol. Later, researchers added stomach acid to the list of causes and began treating ulcers with antacids. Now it is known that peptic ulcers are predominantly caused by Helicobacter pylori, a spiral-shaped bacterium that normally exist in the stomach.
Amphetamine poisoning can cause intravascular coagulation, circulatory collapse, rhabdomyolysis, ischemic colitis, acute psychosis, hyperthermia, respiratory distress syndrome, and pericarditis.
Approximately 500,000 babies are born each year in the United States to teenage mothers.
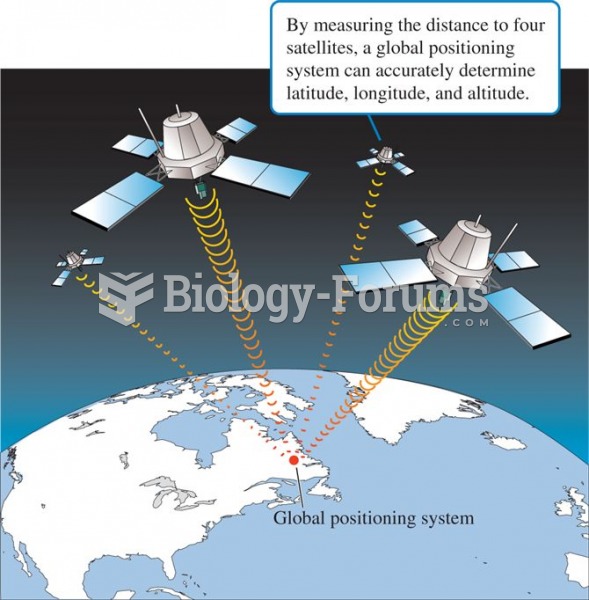 Global positioning systems determine latitude, longitude, and altitude by measuring the distance fro
Global positioning systems determine latitude, longitude, and altitude by measuring the distance fro
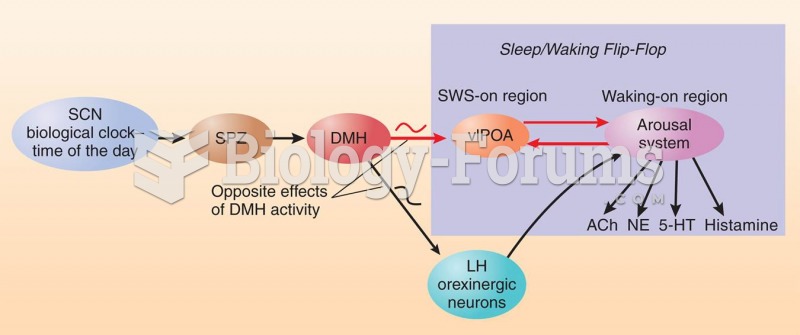 Control of Circadian Rhythms in Sleep and Waking by the SCN During the day cycle, the DMH inhibits t
Control of Circadian Rhythms in Sleep and Waking by the SCN During the day cycle, the DMH inhibits t