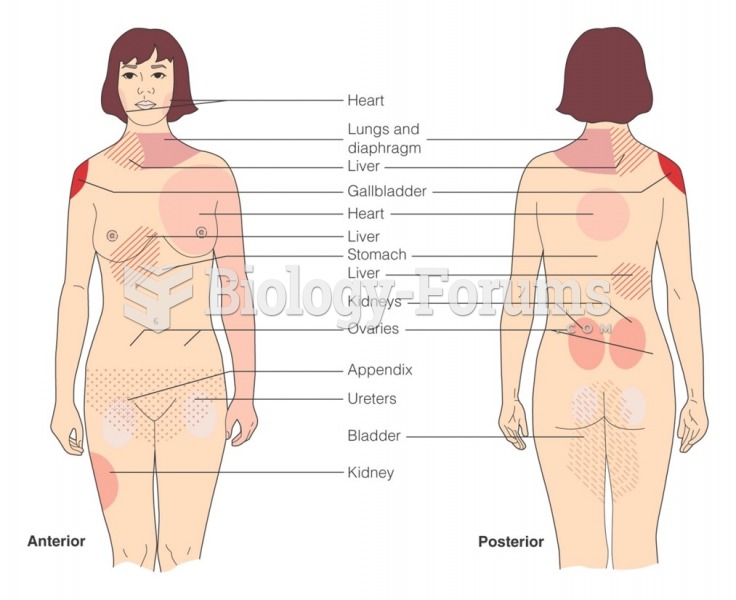
|
|
|
The most common childhood diseases include croup, chickenpox, ear infections, flu, pneumonia, ringworm, respiratory syncytial virus, scabies, head lice, and asthma.
Automated pill dispensing systems have alarms to alert patients when the correct dosing time has arrived. Most systems work with many varieties of medications, so patients who are taking a variety of drugs can still be in control of their dose regimen.
The U.S. Preventive Services Task Force recommends that all women age 65 years of age or older should be screened with bone densitometry.
A recent study has found that following a diet rich in berries may slow down the aging process of the brain. This diet apparently helps to keep dopamine levels much higher than are seen in normal individuals who do not eat berries as a regular part of their diet as they enter their later years.
Fatal fungal infections may be able to resist newer antifungal drugs. Globally, fungal infections are often fatal due to the lack of access to multiple antifungals, which may be required to be utilized in combination. Single antifungals may not be enough to stop a fungal infection from causing the death of a patient.
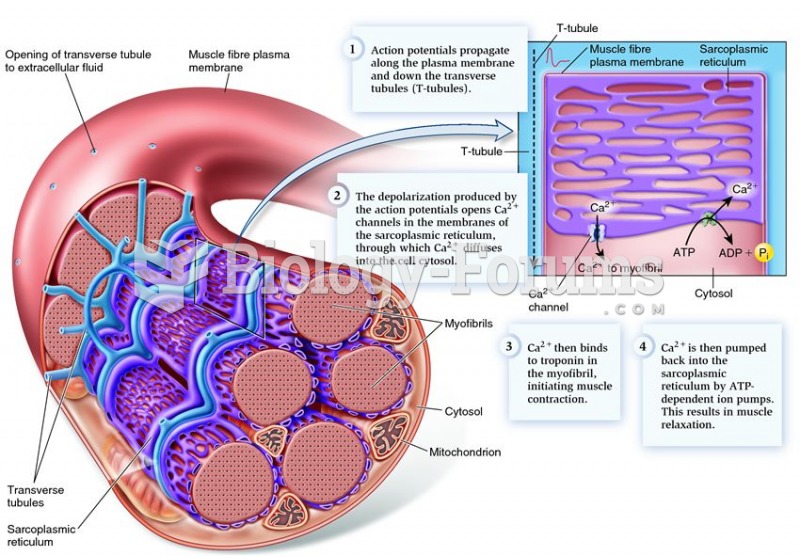 Arrangement of the sarcoplasmic reticulum, transverse tubules, and myofibrils in a single skeletal m
Arrangement of the sarcoplasmic reticulum, transverse tubules, and myofibrils in a single skeletal m
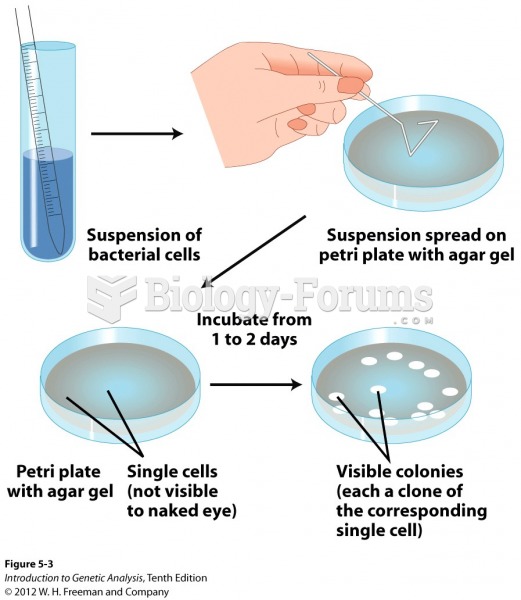 Bacterial colonies, each derived from a single cell Bacterial colonies, each derived from a single c
Bacterial colonies, each derived from a single cell Bacterial colonies, each derived from a single c