|
|
|
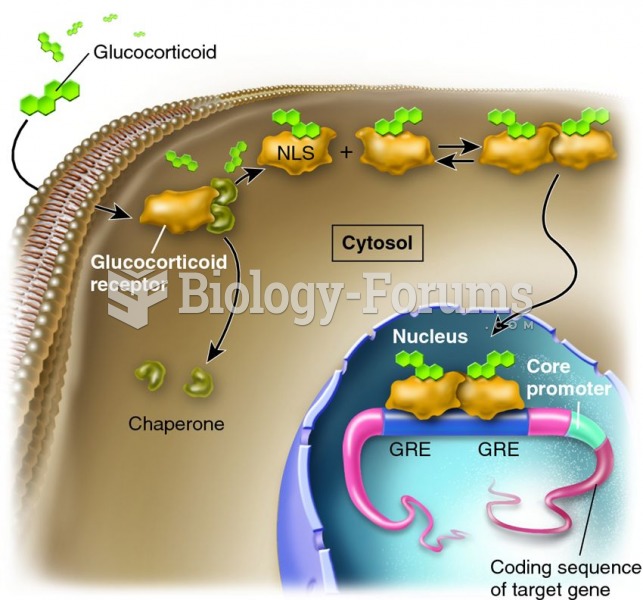
Interferon was scarce and expensive until 1980, when the interferon gene was inserted into bacteria using recombinant DNA technology, allowing for mass cultivation and purification from bacterial cultures.
The most dangerous mercury compound, dimethyl mercury, is so toxic that even a few microliters spilled on the skin can cause death. Mercury has been shown to accumulate in higher amounts in the following types of fish than other types: swordfish, shark, mackerel, tilefish, crab, and tuna.
When blood is deoxygenated and flowing back to the heart through the veins, it is dark reddish-blue in color. Blood in the arteries that is oxygenated and flowing out to the body is bright red. Whereas arterial blood comes out in spurts, venous blood flows.
The top 10 most important tips that will help you grow old gracefully include (1) quit smoking, (2) keep your weight down, (3) take supplements, (4) skip a meal each day or fast 1 day per week, (5) get a pet, (6) get medical help for chronic pain, (7) walk regularly, (8) reduce arguments, (9) put live plants in your living space, and (10) do some weight training.
Serum cholesterol testing in adults is recommended every 1 to 5 years. People with diabetes and a family history of high cholesterol should be tested even more frequently.