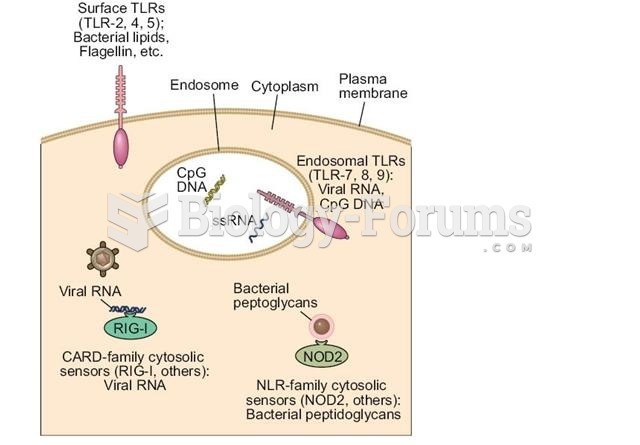
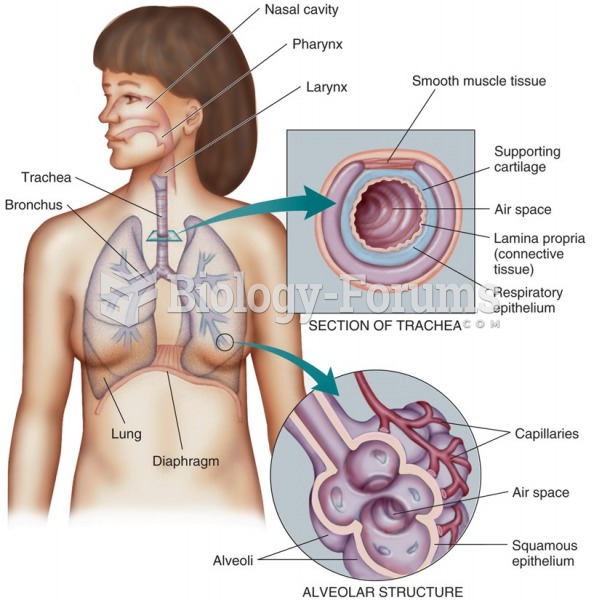
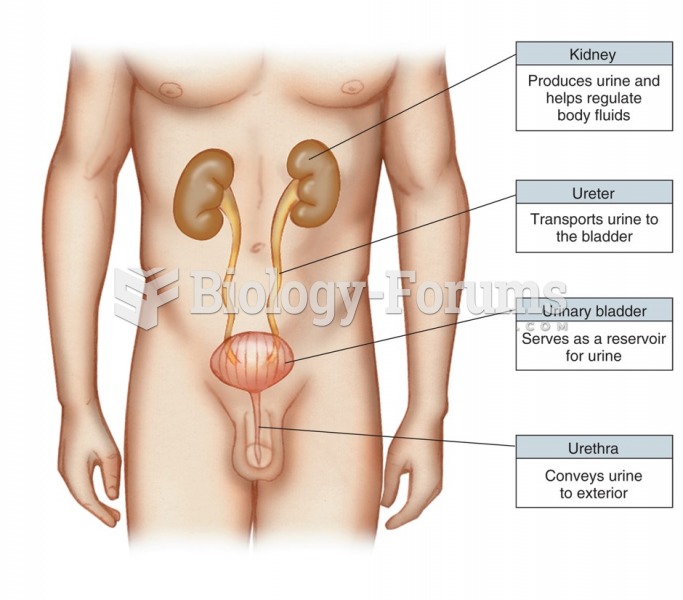
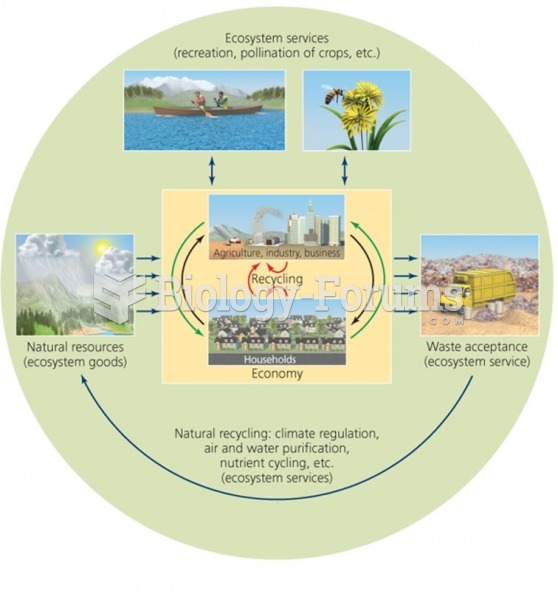
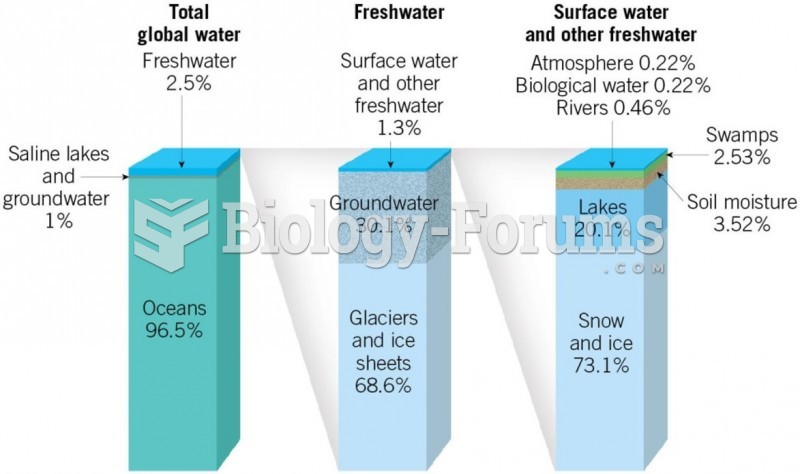
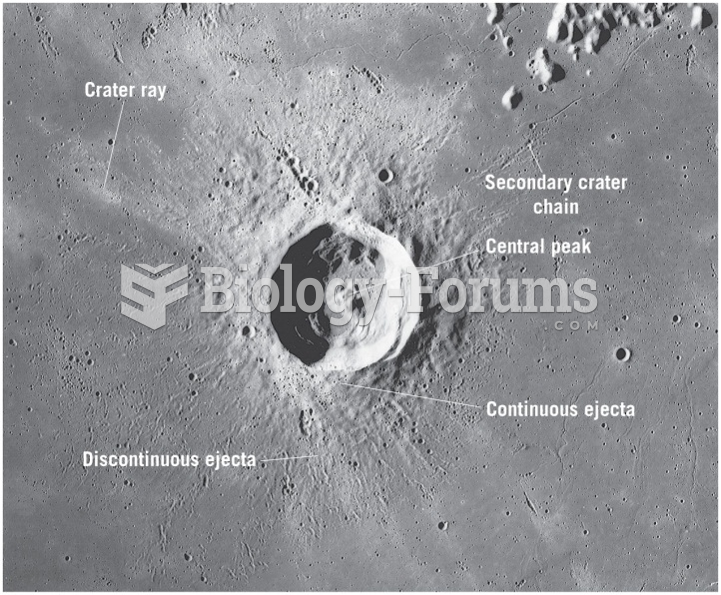
|
|
|
In 2006, a generic antinausea drug named ondansetron was approved. It is used to stop nausea and vomiting associated with surgery, chemotherapy, and radiation therapy.
Carbamazepine can interfere with the results of home pregnancy tests. If you are taking carbamazepine, do not try to test for pregnancy at home.
Many people have small pouches in their colons that bulge outward through weak spots. Each pouch is called a diverticulum. About 10% of Americans older than age 40 years have diverticulosis, which, when the pouches become infected or inflamed, is called diverticulitis. The main cause of diverticular disease is a low-fiber diet.
There used to be a metric calendar, as well as metric clocks. The metric calendar, or "French Republican Calendar" divided the year into 12 months, but each month was divided into three 10-day weeks. Each day had 10 decimal hours. Each hour had 100 decimal minutes. Due to lack of popularity, the metric clocks and calendars were ended in 1795, three years after they had been first marketed.
All adults should have their cholesterol levels checked once every 5 years. During 2009–2010, 69.4% of Americans age 20 and older reported having their cholesterol checked within the last five years.