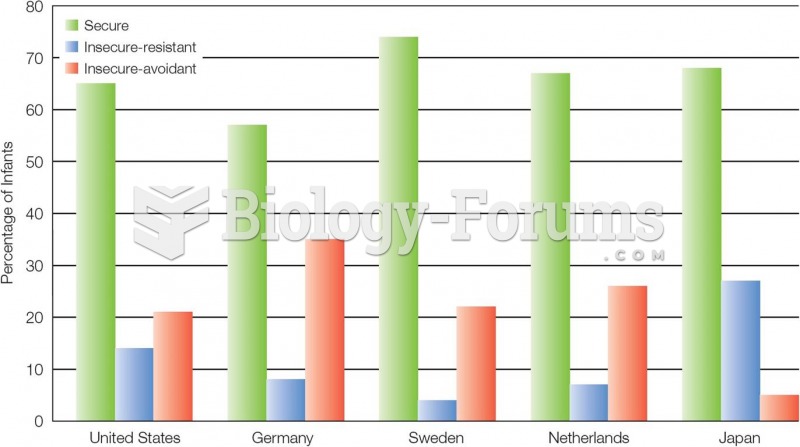
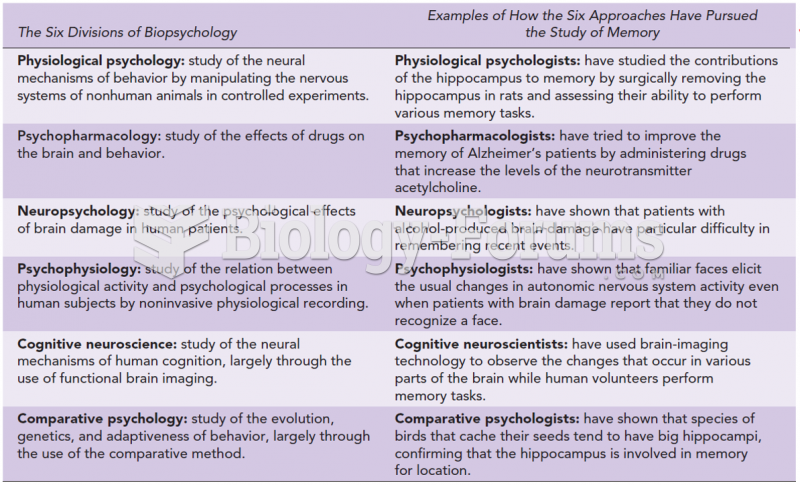
Answer to Question 1
ANS: D
Privacy is an individual's right to determine the time, extent, and general circumstances under which personal information will be shared with or withheld from others. This information consists of one's attitudes, beliefs, behaviors, opinions, and records. The Privacy Act of 1974 provided the initial protection of an individual's privacy. Because of this act, data collection methods were to be scrutinized to protect subjects' privacy, and data cannot be gathered from subjects without their knowledge. Individuals also have the right to access their records and to prevent access by others. The intent of this act was to prevent the invasion of privacy that occurs when private information is shared without an individual's knowledge or against his or her will. Invading an individual's privacy might cause loss of dignity, friendships, or employment or create feelings of anxiety, guilt, embarrassment, or shame. The HIPAA Privacy Rule expanded the protection of an individual's privacy, specifically his or her protected individually identifiable health information, and described the ways in which covered entities can use or disclose this information. De-identifying health data involves removing 18 elements that could be used to identify an individual. An important one on this list is the individual's medical record number. In the example, the researcher's use of an actual patient identification number on a transcription risks the human right to privacy; a code number should have been used instead.
Answer to Question 2
ANS: A
Confidentiality is the researcher's management of private information shared by a subject that must not be shared with others without the authorization of the subject. In the example, sending one research subject the raw data of a different subject is a direct breach of confidentiality. A breach in confidentiality can occur when a researcher, by accident or direct action, allows an unauthorized person to gain access to raw study data. The right to fair treatment is based on the ethical principle of justice. This principle holds that each person should be treated fairly and should receive what he or she is due or owed. The right to protection from discomfort and harm is based on the ethical principle of beneficence, which holds that one should do good and, above all, do no harm.