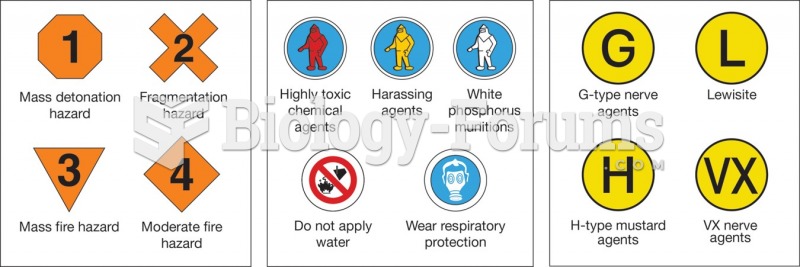
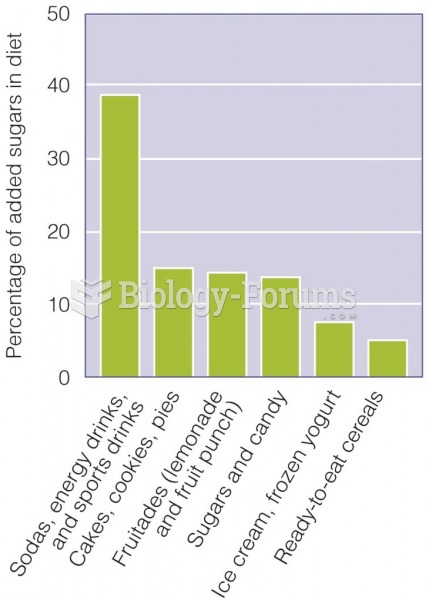
|
|
|
Common abbreviations that cause medication errors include U (unit), mg (milligram), QD (every day), SC (subcutaneous), TIW (three times per week), D/C (discharge or discontinue), HS (at bedtime or "hours of sleep"), cc (cubic centimeters), and AU (each ear).
In most climates, 8 to 10 glasses of water per day is recommended for adults. The best indicator for adequate fluid intake is frequent, clear urination.
Astigmatism is the most common vision problem. It may accompany nearsightedness or farsightedness. It is usually caused by an irregularly shaped cornea, but sometimes it is the result of an irregularly shaped lens. Either type can be corrected by eyeglasses, contact lenses, or refractive surgery.
Hypertension is a silent killer because it is deadly and has no significant early symptoms. The danger from hypertension is the extra load on the heart, which can lead to hypertensive heart disease and kidney damage. This occurs without any major symptoms until the high blood pressure becomes extreme. Regular blood pressure checks are an important method of catching hypertension before it can kill you.
The first oncogene was discovered in 1970 and was termed SRC (pronounced "SARK").
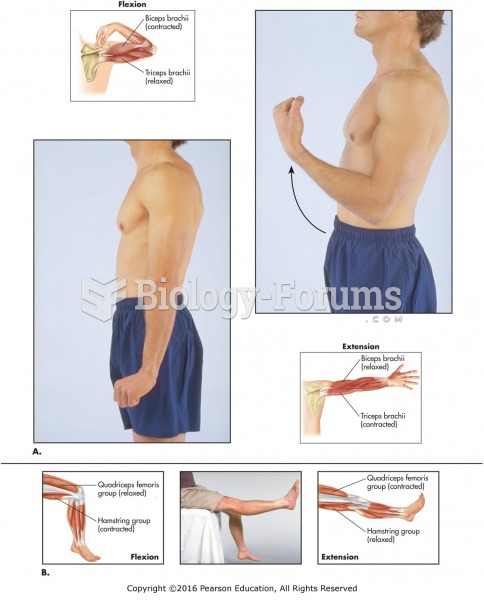 The types of skeletal movement. (A) Flexion and extension of left forearm. (B) Flexion and extension ...
The types of skeletal movement. (A) Flexion and extension of left forearm. (B) Flexion and extension ...
 An additional extension may be necessary to hoist a truck or van equipped with running boards to ...
An additional extension may be necessary to hoist a truck or van equipped with running boards to ...