|
|
|
Only one in 10 cancer deaths is caused by the primary tumor. The vast majority of cancer mortality is caused by cells breaking away from the main tumor and metastasizing to other parts of the body, such as the brain, bones, or liver.
During pregnancy, a woman is more likely to experience bleeding gums and nosebleeds caused by hormonal changes that increase blood flow to the mouth and nose.
Each year in the United States, there are approximately six million pregnancies. This means that at any one time, about 4% of women in the United States are pregnant.
Essential fatty acids have been shown to be effective against ulcers, asthma, dental cavities, and skin disorders such as acne.
For high blood pressure (hypertension), a new class of drug, called a vasopeptidase blocker (inhibitor), has been developed. It decreases blood pressure by simultaneously dilating the peripheral arteries and increasing the body's loss of salt.
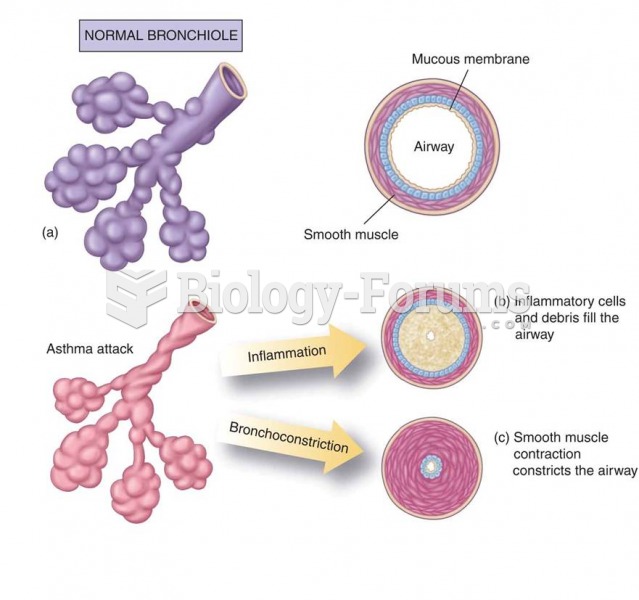 Changes in the bronchioles during an asthma attack: (a) Normal bronchiole; (b) the inflammatory comp
Changes in the bronchioles during an asthma attack: (a) Normal bronchiole; (b) the inflammatory comp
 Used antifreeze coolant should be kept separate and stored in a leakproof container until it can be ...
Used antifreeze coolant should be kept separate and stored in a leakproof container until it can be ...
 A vacuum-operated EGR valve. The vacuum to the EGR valve is computer controlled by the EGR valve ...
A vacuum-operated EGR valve. The vacuum to the EGR valve is computer controlled by the EGR valve ...