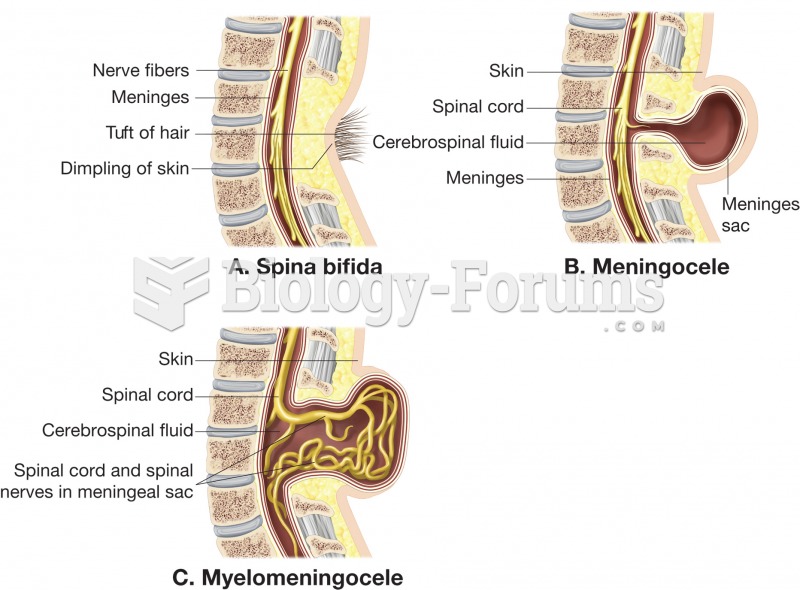
|
|
|
The longest a person has survived after a heart transplant is 24 years.
The Centers for Disease Control and Prevention has released reports detailing the deaths of infants (younger than 1 year of age) who died after being given cold and cough medications. This underscores the importance of educating parents that children younger than 2 years of age should never be given over-the-counter cold and cough medications without consulting their physicians.
A recent study has found that following a diet rich in berries may slow down the aging process of the brain. This diet apparently helps to keep dopamine levels much higher than are seen in normal individuals who do not eat berries as a regular part of their diet as they enter their later years.
All adults should have their cholesterol levels checked once every 5 years. During 2009–2010, 69.4% of Americans age 20 and older reported having their cholesterol checked within the last five years.
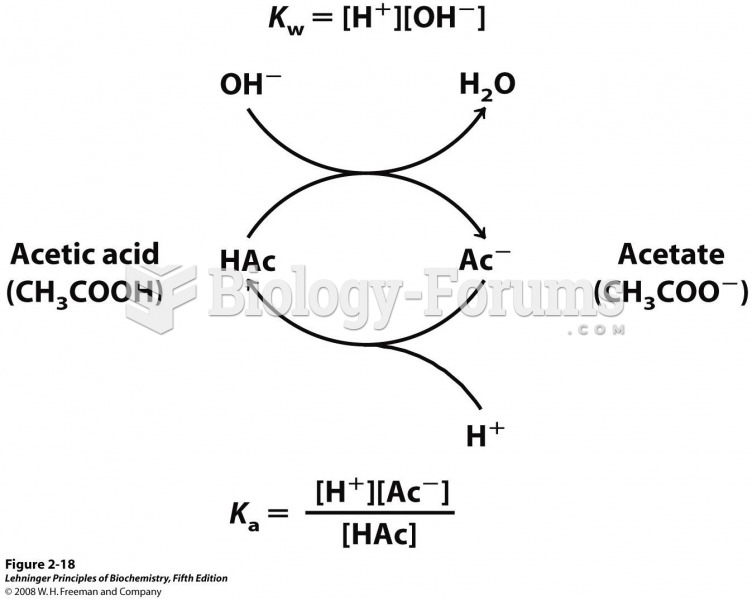
The ratio of hydrogen atoms to oxygen in water (H2O) is 2:1.