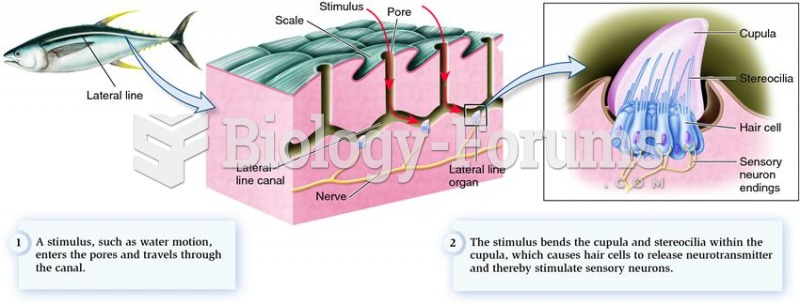
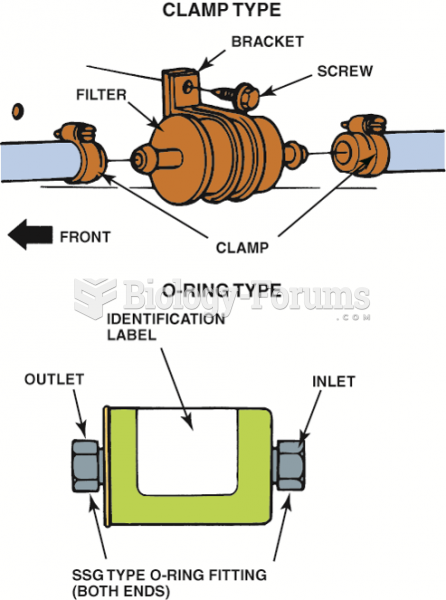
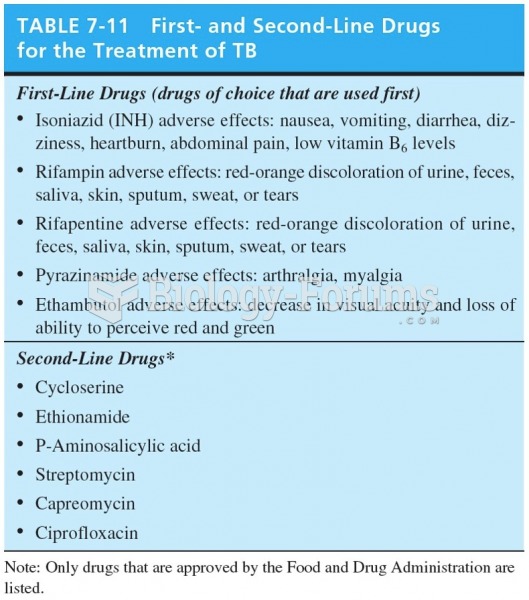
|
|
|
Aspirin may benefit 11 different cancers, including those of the colon, pancreas, lungs, prostate, breasts, and leukemia.
The human body's pharmacokinetics are quite varied. Our hair holds onto drugs longer than our urine, blood, or saliva. For example, alcohol can be detected in the hair for up to 90 days after it was consumed. The same is true for marijuana, cocaine, ecstasy, heroin, methamphetamine, and nicotine.
A good example of polar molecules can be understood when trying to make a cake. If water and oil are required, they will not mix together. If you put them into a measuring cup, the oil will rise to the top while the water remains on the bottom.
The first monoclonal antibodies were made exclusively from mouse cells. Some are now fully human, which means they are likely to be safer and may be more effective than older monoclonal antibodies.
For high blood pressure (hypertension), a new class of drug, called a vasopeptidase blocker (inhibitor), has been developed. It decreases blood pressure by simultaneously dilating the peripheral arteries and increasing the body's loss of salt.