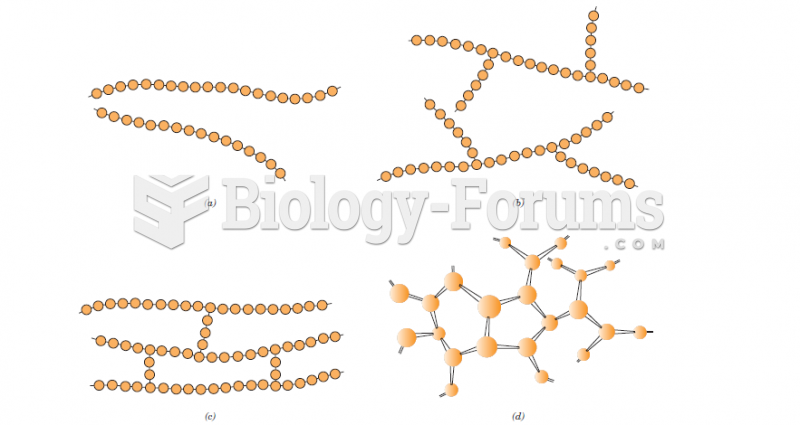
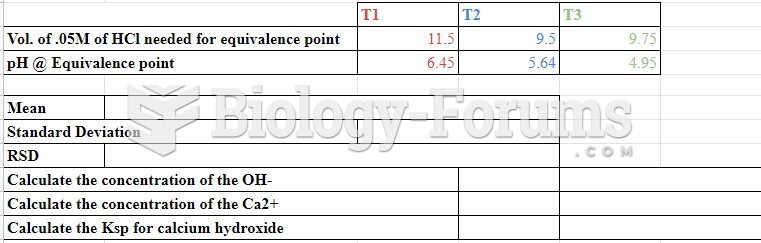
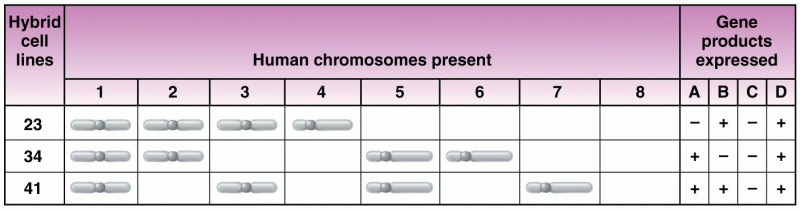
|
|
|
As of mid-2016, 18.2 million people were receiving advanced retroviral therapy (ART) worldwide. This represents between 43–50% of the 34–39.8 million people living with HIV.
It is difficult to obtain enough calcium without consuming milk or other dairy foods.
As many as 20% of Americans have been infected by the fungus known as Histoplasmosis. While most people are asymptomatic or only have slight symptoms, infection can progress to a rapid and potentially fatal superinfection.
There are actually 60 minerals, 16 vitamins, 12 essential amino acids, and three essential fatty acids that your body needs every day.
Drugs are in development that may cure asthma and hay fever once and for all. They target leukotrienes, which are known to cause tightening of the air passages in the lungs and increase mucus productions in nasal passages.