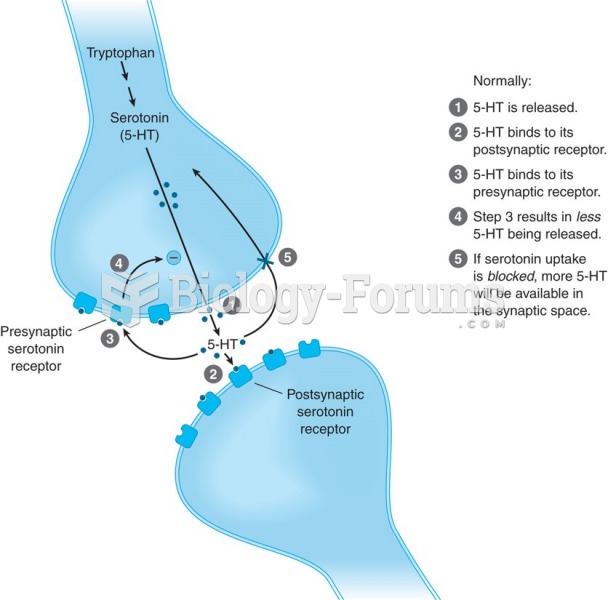
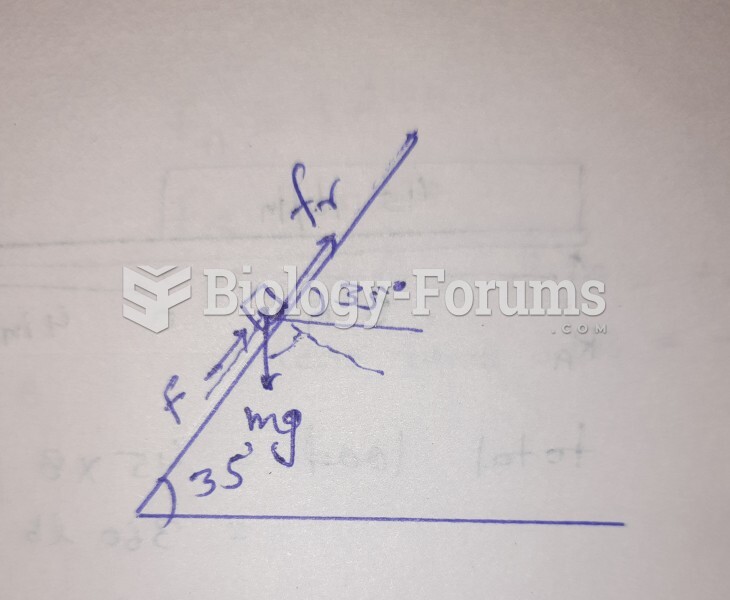
|
|
|
Though “Krazy Glue” or “Super Glue” has the ability to seal small wounds, it is not recommended for this purpose since it contains many substances that should not enter the body through the skin, and may be harmful.
When blood is deoxygenated and flowing back to the heart through the veins, it is dark reddish-blue in color. Blood in the arteries that is oxygenated and flowing out to the body is bright red. Whereas arterial blood comes out in spurts, venous blood flows.
Though the United States has largely rejected the metric system, it is used for currency, as in 100 pennies = 1 dollar. Previously, the British currency system was used, with measurements such as 12 pence to the shilling, and 20 shillings to the pound.
Colchicine is a highly poisonous alkaloid originally extracted from a type of saffron plant that is used mainly to treat gout.
To combat osteoporosis, changes in lifestyle and diet are recommended. At-risk patients should include 1,200 to 1,500 mg of calcium daily either via dietary means or with supplements.
 Examples of four letter formats: (A) block style, (B) modified block style, (C) modified block style ...
Examples of four letter formats: (A) block style, (B) modified block style, (C) modified block style ...
 Two stubby screwdrivers used to access screws that have limited space above. A straight blade is on ...
Two stubby screwdrivers used to access screws that have limited space above. A straight blade is on ...