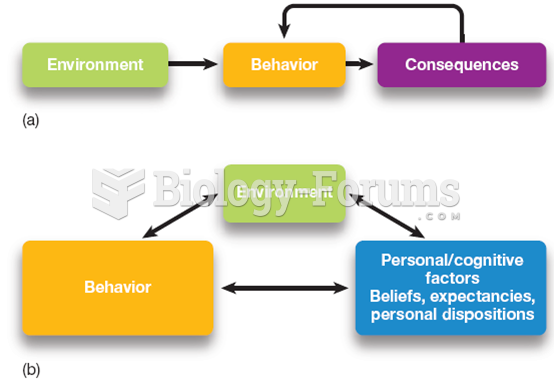
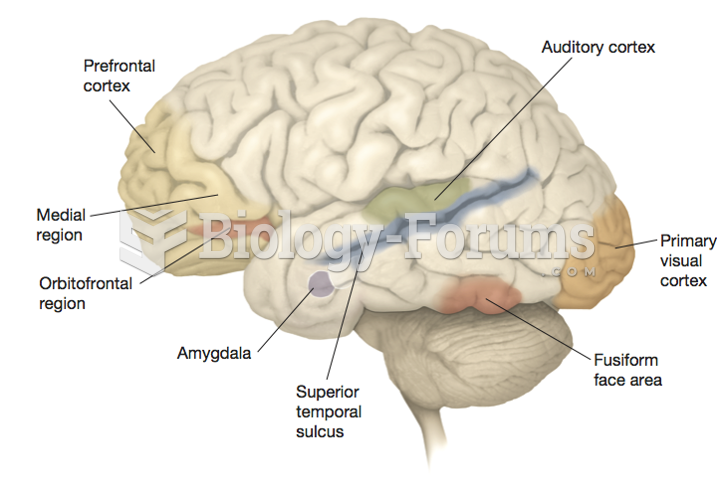
|
|
|
Persons who overdose with cardiac glycosides have a better chance of overall survival if they can survive the first 24 hours after the overdose.
Allergies play a major part in the health of children. The most prevalent childhood allergies are milk, egg, soy, wheat, peanuts, tree nuts, and seafood.
Approximately 70% of expectant mothers report experiencing some symptoms of morning sickness during the first trimester of pregnancy.
The human body's pharmacokinetics are quite varied. Our hair holds onto drugs longer than our urine, blood, or saliva. For example, alcohol can be detected in the hair for up to 90 days after it was consumed. The same is true for marijuana, cocaine, ecstasy, heroin, methamphetamine, and nicotine.
In 1886, William Bates reported on the discovery of a substance produced by the adrenal gland that turned out to be epinephrine (adrenaline). In 1904, this drug was first artificially synthesized by Friedrich Stolz.