|
|
|
It is difficult to obtain enough calcium without consuming milk or other dairy foods.
Adults are resistant to the bacterium that causes Botulism. These bacteria thrive in honey – therefore, honey should never be given to infants since their immune systems are not yet resistant.
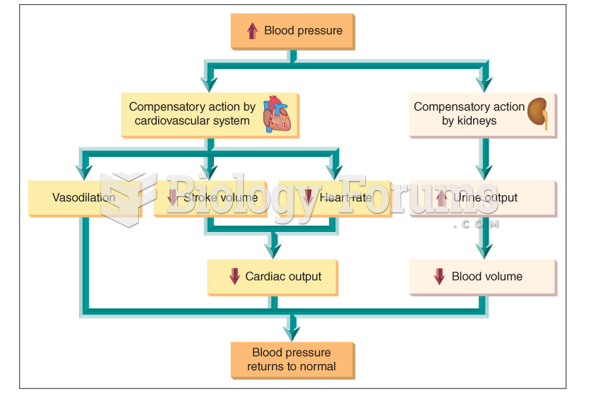
Studies show that systolic blood pressure can be significantly lowered by taking statins. In fact, the higher the patient's baseline blood pressure, the greater the effect of statins on his or her blood pressure.
When blood is deoxygenated and flowing back to the heart through the veins, it is dark reddish-blue in color. Blood in the arteries that is oxygenated and flowing out to the body is bright red. Whereas arterial blood comes out in spurts, venous blood flows.
Of the estimated 2 million heroin users in the United States, 600,000–800,000 are considered hardcore addicts. Heroin addiction is considered to be one of the hardest addictions to recover from.