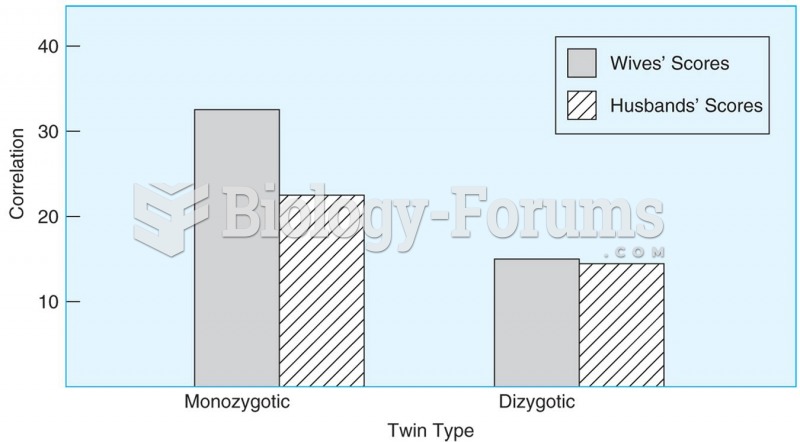
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
Human kidneys will clean about 1 million gallons of blood in an average lifetime.
Did you know?
Famous people who died from poisoning or drug overdose include, Adolf Hitler, Socrates, Juan Ponce de Leon, Marilyn Monroe, Judy Garland, and John Belushi.
Did you know?
When blood is exposed to air, it clots. Heparin allows the blood to come in direct contact with air without clotting.
Did you know?
About 100 new prescription or over-the-counter drugs come into the U.S. market every year.
Did you know?
Though “Krazy Glue” or “Super Glue” has the ability to seal small wounds, it is not recommended for this purpose since it contains many substances that should not enter the body through the skin, and may be harmful.