|
|
|
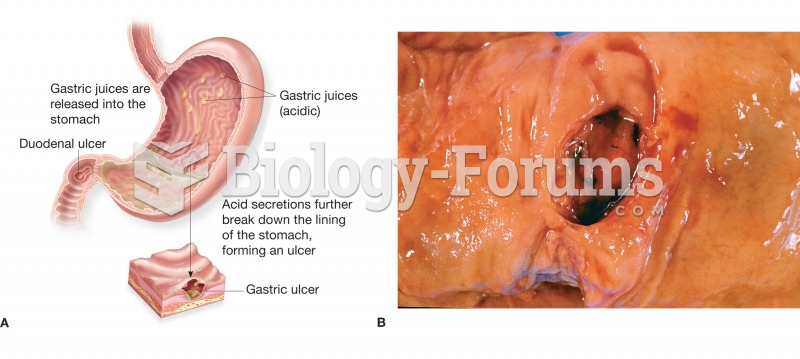
On average, the stomach produces 2 L of hydrochloric acid per day.
ACTH levels are normally highest in the early morning (between 6 and 8 A.M.) and lowest in the evening (between 6 and 11 P.M.). Therefore, a doctor who suspects abnormal levels looks for low ACTH in the morning and high ACTH in the evening.
Children with strabismus (crossed eyes) can be treated. They are not able to outgrow this condition on their own, but with help, it can be more easily corrected at a younger age. It is important for infants to have eye examinations as early as possible in their development and then another at age 2 years.
Symptoms of kidney problems include a loss of appetite, back pain (which may be sudden and intense), chills, abdominal pain, fluid retention, nausea, the urge to urinate, vomiting, and fever.
When Gabriel Fahrenheit invented the first mercury thermometer, he called "zero degrees" the lowest temperature he was able to attain with a mixture of ice and salt. For the upper point of his scale, he used 96°, which he measured as normal human body temperature (we know it to be 98.6° today because of more accurate thermometers).