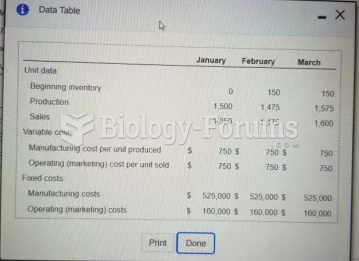
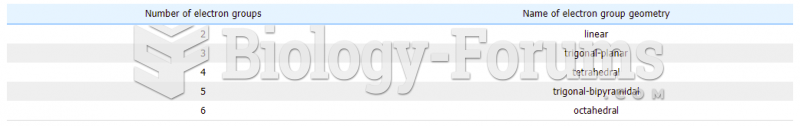
Answer to Question 1
Symmetric key cryptography involves the use of a secret cipher that transforms plain text into cipher text. Both the sender and the receiver use the same key to encrypt and decrypt the message. The possibilities for simple substitution and transposition ciphers are endless, but there are several flaws in these types of systems that make them inadequate for use today. First, for the sender and the receiver to have the same key, it must be sent over a communication medium that is insecure or they must meet in person to exchange the key. If the secret key is lost or stolen, the encryption system fails. This method can be used effectively for data storage protection, but is less convenient for e-mail since the correspondents must pass the secret key to one another over another secure medium prior to commencing the communication. Second, in the digital age, computers are so fast and powerful that these ancient encryption techniques can be quickly and easily broken. Modern digital encryption systems must use keys with between 56 and 512 binary digits to ensure that decryption would be unlikely. Third, for commercial use on an e-commerce site each of the parties in a transaction would need a secret key. In a population of millions of Internet users, thousands of millions of keys would be needed to accommodate all e-commerce customers.
Public key cryptography solves the problem of exchanging keys. In this method every user has a pair of numeric keys: private and public. The public key is not secret; on the contrary, it is supposed to be disseminated widely. Public keys may be published in company catalogs or on online. The public key is used by outside parties to encrypt the messages addressed to you. The private or secret key is used by the recipient to decipher incoming messages. The main advantage of a public key cryptographic system is its ability to begin secure correspondence over the Internet without prior exchanging of the keys and, therefore, without the need for a meeting in person or using conventional carriers for key exchange.
Encryption can provide four of the six key dimensions of e-commerce security. It can provide assurance that the message has not been altered (integrity), prevent the user from denying that he/she has sent the message (nonrepudiation), provide verification of the identity of the message (authentication), and give assurance that the message has not been read by others (confidentiality).
Answer to Question 2
TRUE