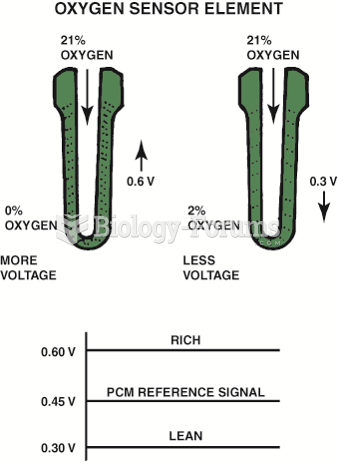
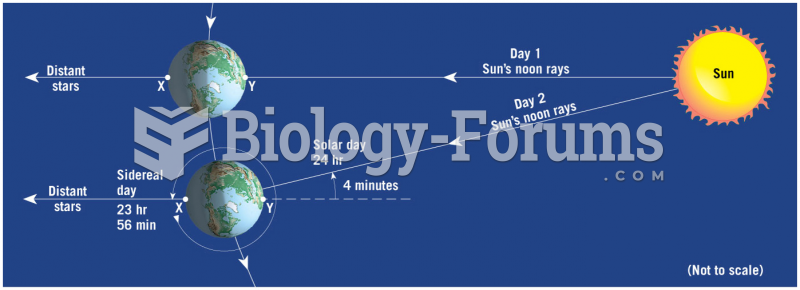
|
|
|
Illness; diuretics; laxative abuse; hot weather; exercise; sweating; caffeine; alcoholic beverages; starvation diets; inadequate carbohydrate consumption; and diets high in protein, salt, or fiber can cause people to become dehydrated.
Blastomycosis is often misdiagnosed, resulting in tragic outcomes. It is caused by a fungus living in moist soil, in wooded areas of the United States and Canada. If inhaled, the fungus can cause mild breathing problems that may worsen and cause serious illness and even death.
Automated pill dispensing systems have alarms to alert patients when the correct dosing time has arrived. Most systems work with many varieties of medications, so patients who are taking a variety of drugs can still be in control of their dose regimen.
The most dangerous mercury compound, dimethyl mercury, is so toxic that even a few microliters spilled on the skin can cause death. Mercury has been shown to accumulate in higher amounts in the following types of fish than other types: swordfish, shark, mackerel, tilefish, crab, and tuna.
Anesthesia awareness is a potentially disturbing adverse effect wherein patients who have been paralyzed with muscle relaxants may awaken. They may be aware of their surroundings but unable to communicate or move. Neurologic monitoring equipment that helps to more closely check the patient's anesthesia stages is now available to avoid the occurrence of anesthesia awareness.
 At breakfast, a middle-class husband sits absorbed in the newspaper and the public affairs of the da
At breakfast, a middle-class husband sits absorbed in the newspaper and the public affairs of the da
 This girl ran four spinning machines in a cotton mill in Whitnel, North Carolina. Only 4 feet, 3 inc
This girl ran four spinning machines in a cotton mill in Whitnel, North Carolina. Only 4 feet, 3 inc