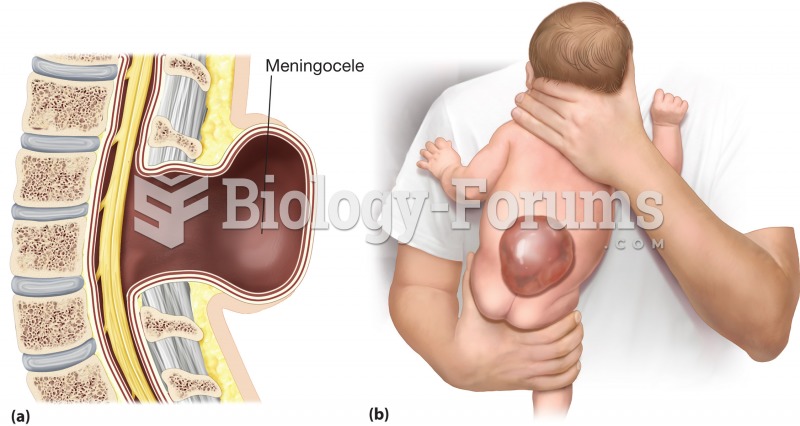
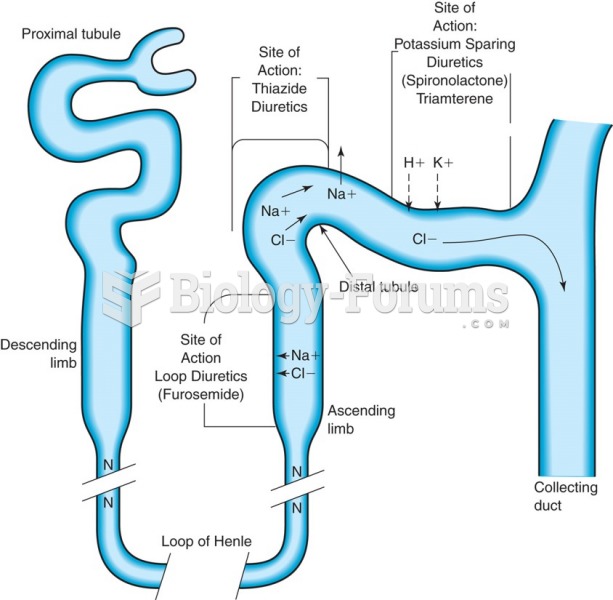
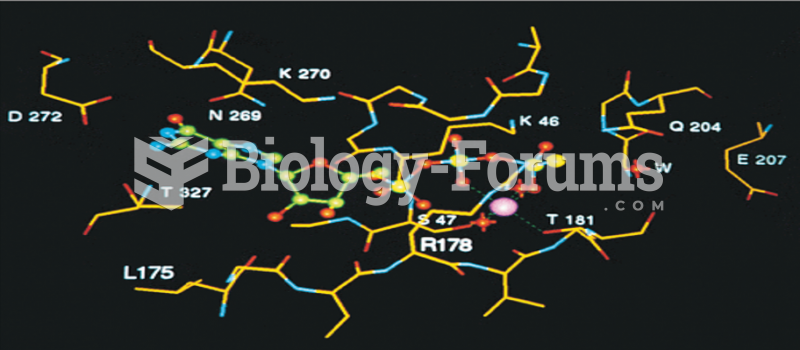
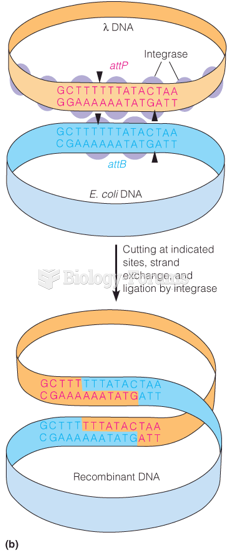
|
|
|
Did you know?
According to research, pregnant women tend to eat more if carrying a baby boy. Male fetuses may secrete a chemical that stimulates their mothers to step up her energy intake.
Did you know?
In the United States, there is a birth every 8 seconds, according to the U.S. Census Bureau's Population Clock.
Did you know?
Green tea is able to stop the scent of garlic or onion from causing bad breath.
Did you know?
A recent study has found that following a diet rich in berries may slow down the aging process of the brain. This diet apparently helps to keep dopamine levels much higher than are seen in normal individuals who do not eat berries as a regular part of their diet as they enter their later years.
Did you know?
Women are 50% to 75% more likely than men to experience an adverse drug reaction.