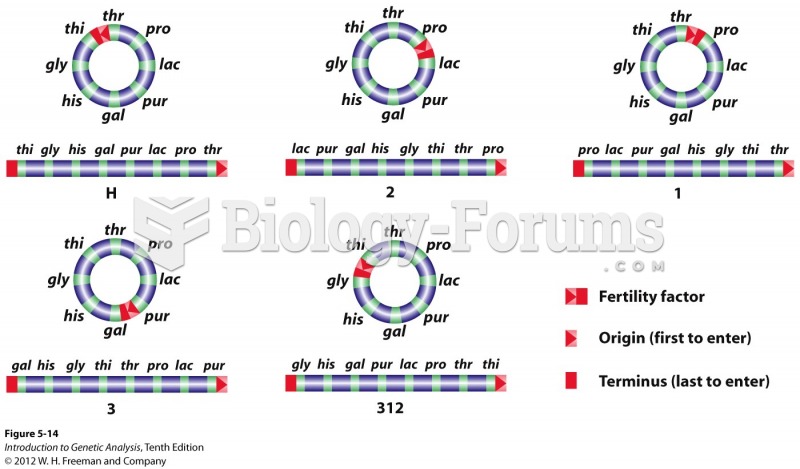
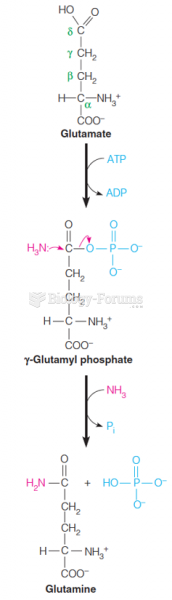
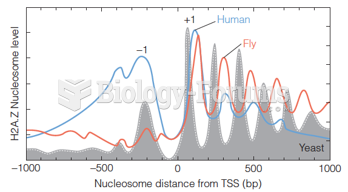
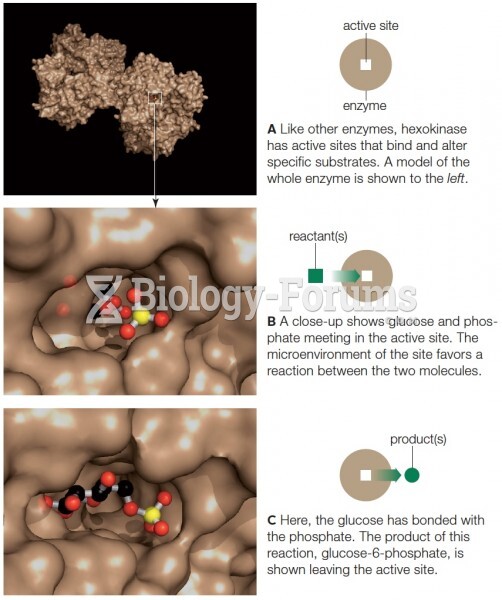
|
|
|
By definition, when a medication is administered intravenously, its bioavailability is 100%.
Alzheimer's disease affects only about 10% of people older than 65 years of age. Most forms of decreased mental function and dementia are caused by disuse (letting the mind get lazy).
Malaria mortality rates are falling. Increased malaria prevention and control measures have greatly improved these rates. Since 2000, malaria mortality rates have fallen globally by 60% among all age groups, and by 65% among children under age 5.
The first monoclonal antibodies were made exclusively from mouse cells. Some are now fully human, which means they are likely to be safer and may be more effective than older monoclonal antibodies.
Serum cholesterol testing in adults is recommended every 1 to 5 years. People with diabetes and a family history of high cholesterol should be tested even more frequently.