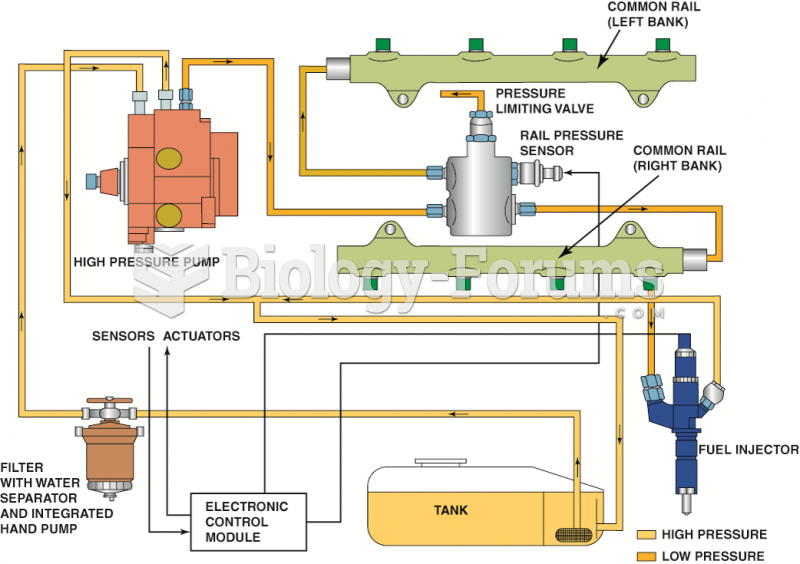
|
|
|
Calcitonin is a naturally occurring hormone. In women who are at least 5 years beyond menopause, it slows bone loss and increases spinal bone density.
Certain topical medications such as clotrimazole and betamethasone are not approved for use in children younger than 12 years of age. They must be used very cautiously, as directed by a doctor, to treat any child. Children have a much greater response to topical steroid medications.
Normal urine is sterile. It contains fluids, salts, and waste products. It is free of bacteria, viruses, and fungi.
The human body's pharmacokinetics are quite varied. Our hair holds onto drugs longer than our urine, blood, or saliva. For example, alcohol can be detected in the hair for up to 90 days after it was consumed. The same is true for marijuana, cocaine, ecstasy, heroin, methamphetamine, and nicotine.
The Centers for Disease Control and Prevention (CDC) was originally known as the Communicable Disease Center, which was formed to fight malaria. It was originally headquartered in Atlanta, Georgia, since the Southern states faced the worst threat from malaria.