|
|
|
Although the Roman numeral for the number 4 has always been taught to have been "IV," according to historians, the ancient Romans probably used "IIII" most of the time. This is partially backed up by the fact that early grandfather clocks displayed IIII for the number 4 instead of IV. Early clockmakers apparently thought that the IIII balanced out the VIII (used for the number 8) on the clock face and that it just looked better.
As the western states of America were settled, pioneers often had to drink rancid water from ponds and other sources. This often resulted in chronic diarrhea, causing many cases of dehydration and death that could have been avoided if clean water had been available.
The Babylonians wrote numbers in a system that used 60 as the base value rather than the number 10. They did not have a symbol for "zero."
Medication errors are more common among seriously ill patients than with those with minor conditions.
Liver spots have nothing whatsoever to do with the liver. They are a type of freckles commonly seen in older adults who have been out in the sun without sufficient sunscreen.
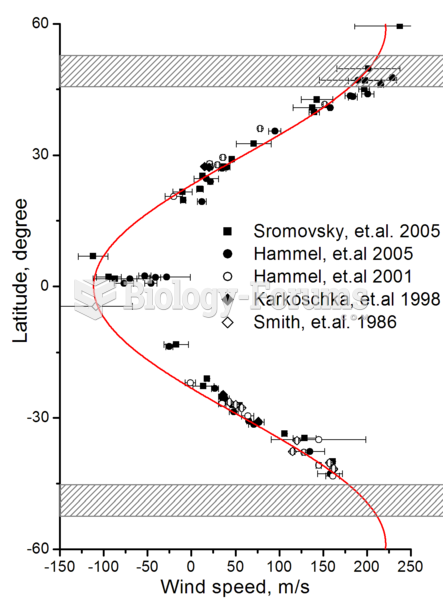 Zonal wind speeds on Uranus. Shaded areas show the southern collar and its future northern counterpa
Zonal wind speeds on Uranus. Shaded areas show the southern collar and its future northern counterpa
 Edward Bellamy, author of the utopian novel Looking Backward (1888) Bellamy’s socialism worried many
Edward Bellamy, author of the utopian novel Looking Backward (1888) Bellamy’s socialism worried many