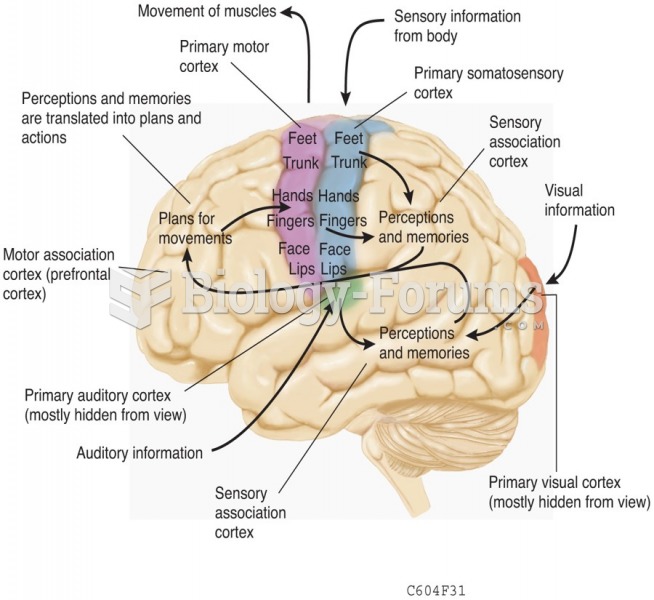
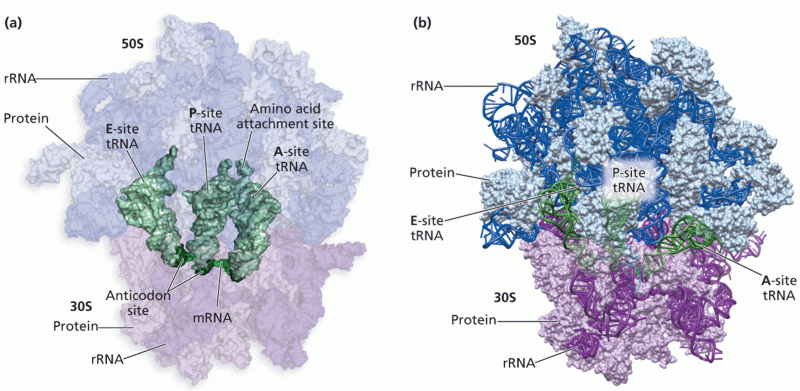
|
|
|
Though Candida and Aspergillus species are the most common fungal pathogens causing invasive fungal disease in the immunocompromised, infections due to previously uncommon hyaline and dematiaceous filamentous fungi are occurring more often today. Rare fungal infections, once accurately diagnosed, may require surgical debridement, immunotherapy, and newer antifungals used singly or in combination with older antifungals, on a case-by-case basis.
Approximately one in three babies in the United States is now delivered by cesarean section. The number of cesarean sections in the United States has risen 46% since 1996.
Persons who overdose with cardiac glycosides have a better chance of overall survival if they can survive the first 24 hours after the overdose.
Today, nearly 8 out of 10 pregnant women living with HIV (about 1.1 million), receive antiretrovirals.
For high blood pressure (hypertension), a new class of drug, called a vasopeptidase blocker (inhibitor), has been developed. It decreases blood pressure by simultaneously dilating the peripheral arteries and increasing the body's loss of salt.