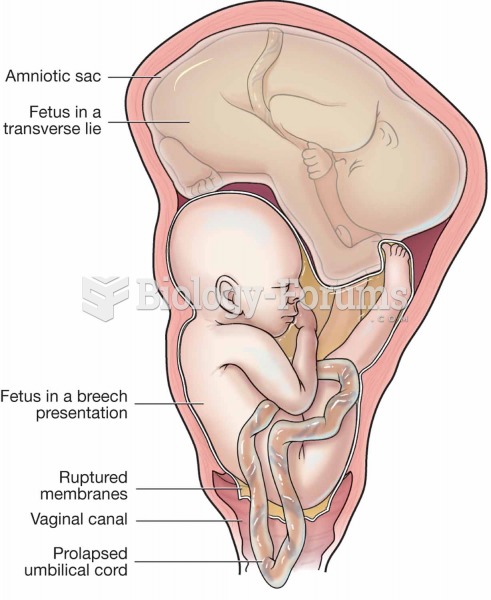
|
|
|
Tobacco depletes the body of vitamins A, C, and E, which can result in any of the following: dry hair, dry skin, dry eyes, poor growth, night blindness, abscesses, insomnia, fatigue, reproductive system problems, sinusitis, pneumonia, frequent respiratory problems, skin disorders, weight loss, rickets, osteomalacia, nervousness, muscle spasms, leg cramps, extremity numbness, bone malformations, decayed teeth, difficulty in walking, irritability, restlessness, profuse sweating, increased uric acid (gout), joint damage, damaged red blood cells, destruction of nerves, infertility, miscarriage, and many types of cancer.
More than 34,000 trademarked medication names and more than 10,000 generic medication names are in use in the United States.
The first documented use of surgical anesthesia in the United States was in Connecticut in 1844.
In 1835 it was discovered that a disease of silkworms known as muscardine could be transferred from one silkworm to another, and was caused by a fungus.
Drugs are in development that may cure asthma and hay fever once and for all. They target leukotrienes, which are known to cause tightening of the air passages in the lungs and increase mucus productions in nasal passages.