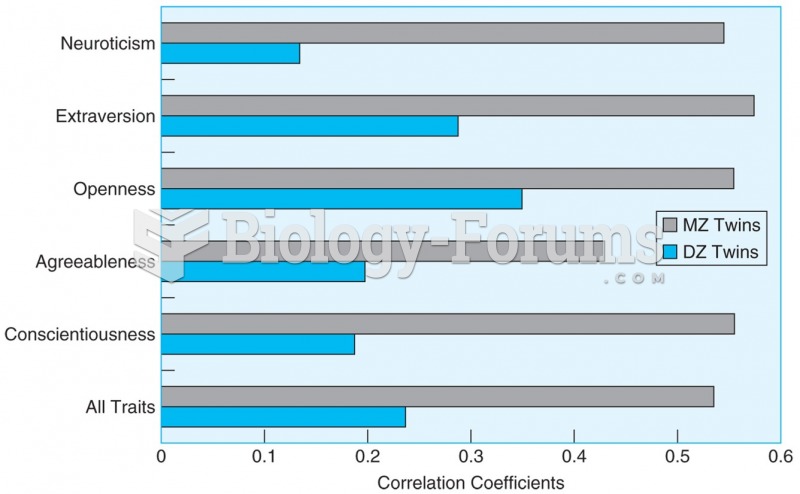
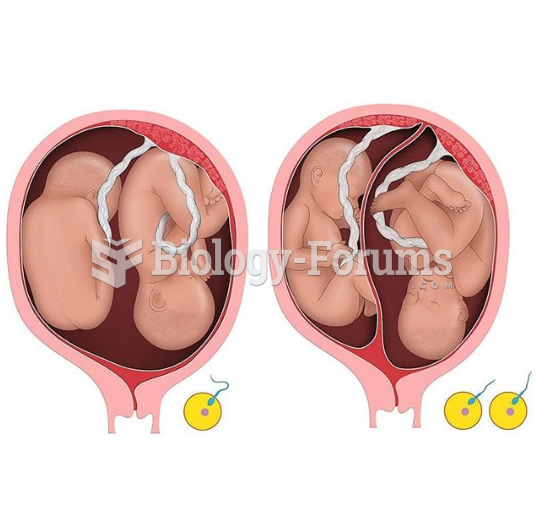
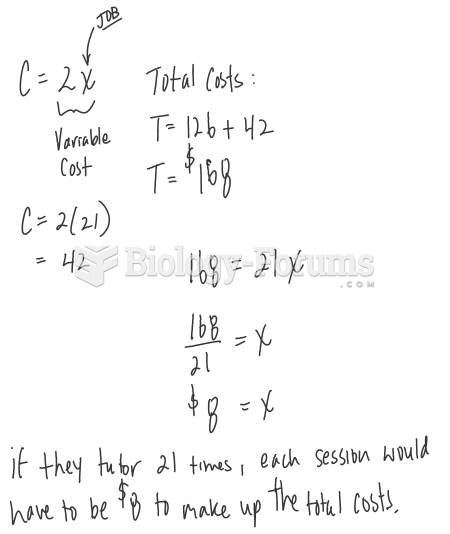|
|
|
About 60% of newborn infants in the United States are jaundiced; that is, they look yellow. Kernicterus is a form of brain damage caused by excessive jaundice. When babies begin to be affected by excessive jaundice and begin to have brain damage, they become excessively lethargic.
Egg cells are about the size of a grain of sand. They are formed inside of a female's ovaries before she is even born.
Individuals are never “cured” of addictions. Instead, they learn how to manage their disease to lead healthy, balanced lives.
In ancient Rome, many of the richer people in the population had lead-induced gout. The reason for this is unclear. Lead poisoning has also been linked to madness.
About one in five American adults and teenagers have had a genital herpes infection—and most of them don't know it. People with genital herpes have at least twice the risk of becoming infected with HIV if exposed to it than those people who do not have genital herpes.