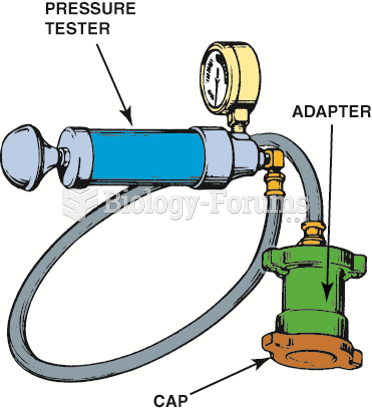
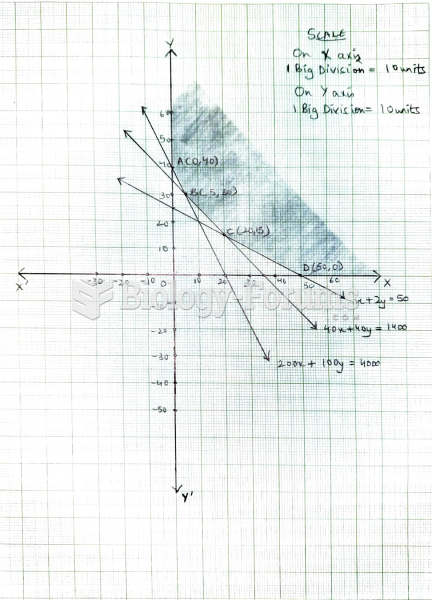
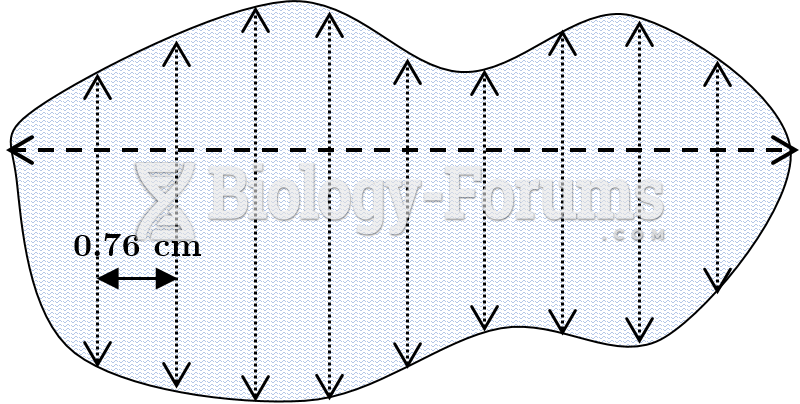
|
|
|
A headache when you wake up in the morning is indicative of sinusitis. Other symptoms of sinusitis can include fever, weakness, tiredness, a cough that may be more severe at night, and a runny nose or nasal congestion.
Methicillin-resistant Staphylococcus aureus or MRSA was discovered in 1961 in the United Kingdom. It if often referred to as a superbug. MRSA infections cause more deaths in the United States every year than AIDS.
Long-term mental and physical effects from substance abuse include: paranoia, psychosis, immune deficiencies, and organ damage.
Acetaminophen (Tylenol) in overdose can seriously damage the liver. It should never be taken by people who use alcohol heavily; it can result in severe liver damage and even a condition requiring a liver transplant.
Excessive alcohol use costs the country approximately $235 billion every year.