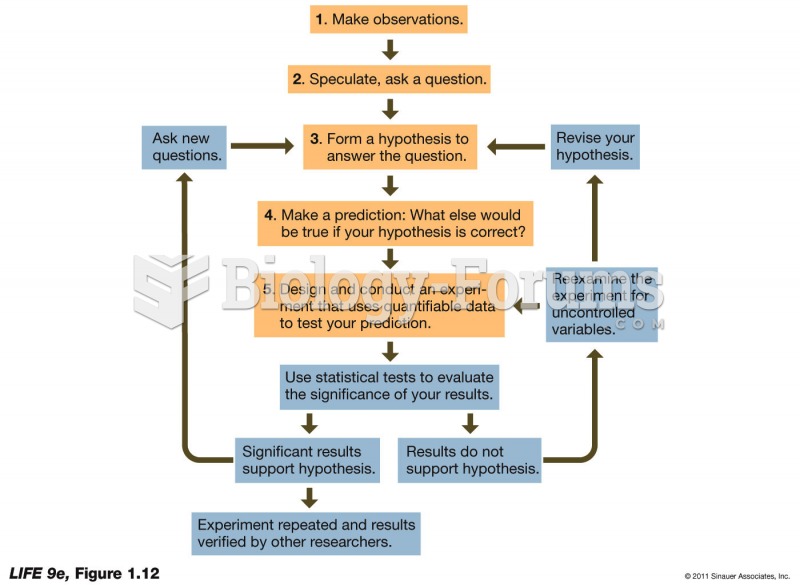
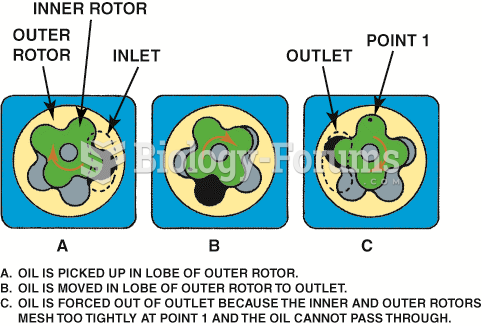
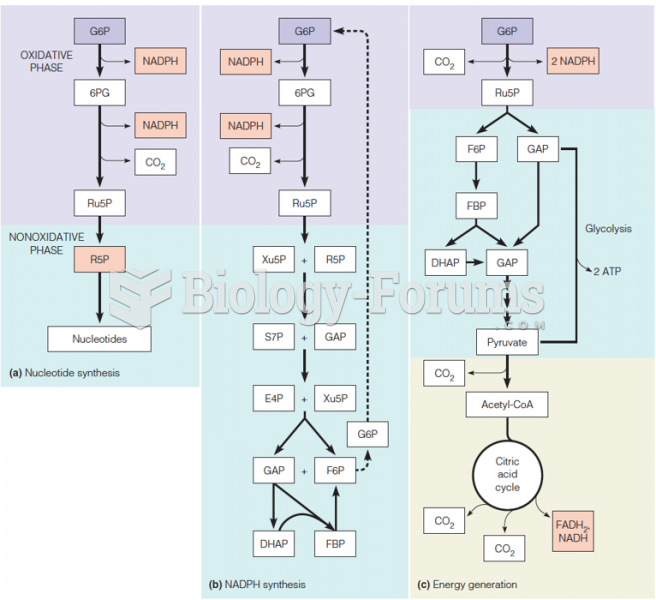
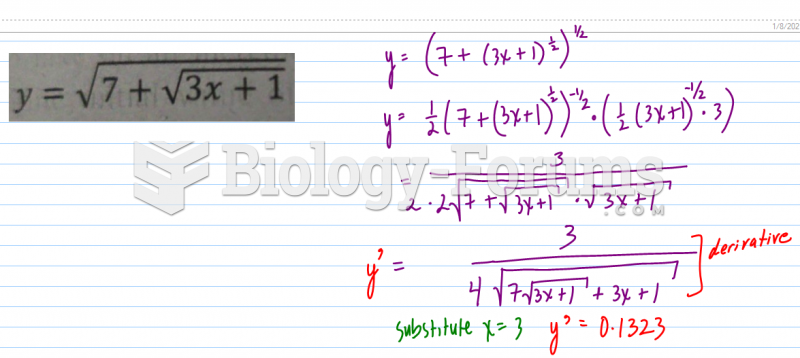|
|
|
Drug-induced pharmacodynamic effects manifested in older adults include drug-induced renal toxicity, which can be a major factor when these adults are experiencing other kidney problems.
Ether was used widely for surgeries but became less popular because of its flammability and its tendency to cause vomiting. In England, it was quickly replaced by chloroform, but this agent caused many deaths and lost popularity.
People with high total cholesterol have about two times the risk for heart disease as people with ideal levels.
Human neurons are so small that they require a microscope in order to be seen. However, some neurons can be up to 3 feet long, such as those that extend from the spinal cord to the toes.
Illicit drug use costs the United States approximately $181 billion every year.