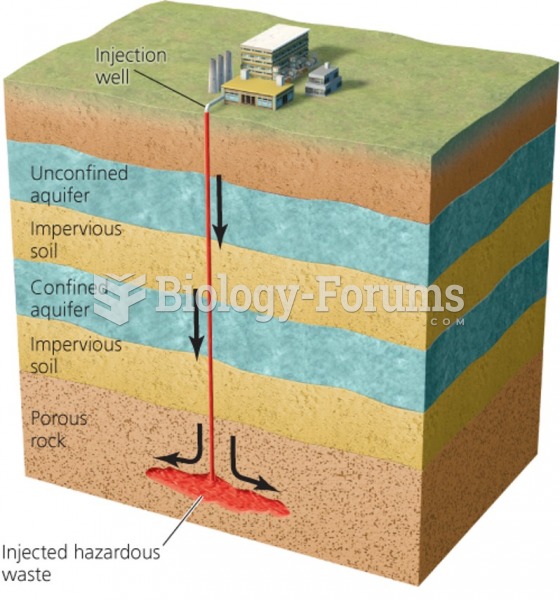
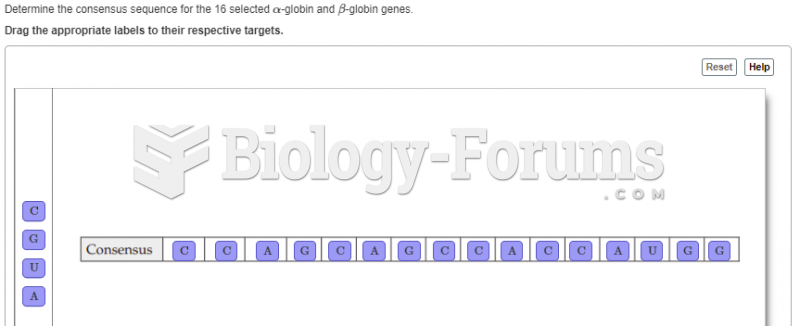
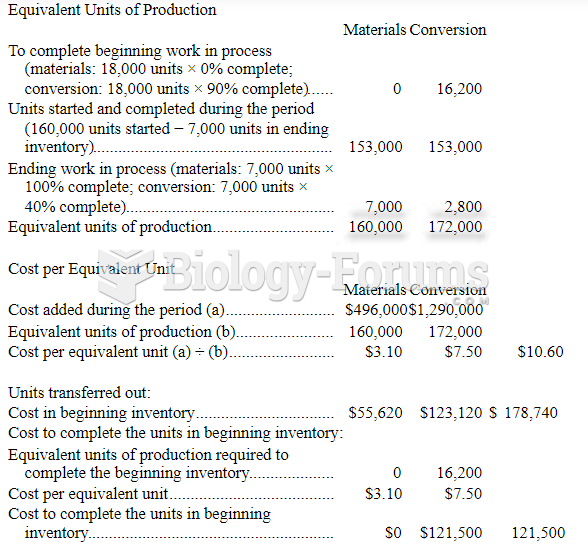
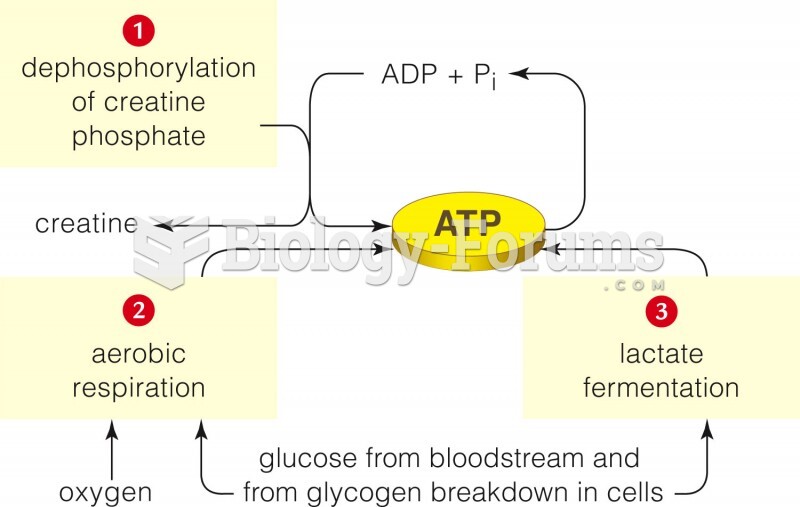
|
|
|
Thyroid conditions cause a higher risk of fibromyalgia and chronic fatigue syndrome.
Asthma attacks and symptoms usually get started by specific triggers (such as viruses, allergies, gases, and air particles). You should talk to your doctor about these triggers and find ways to avoid or get rid of them.
The lipid bilayer is made of phospholipids. They are arranged in a double layer because one of their ends is attracted to water while the other is repelled by water.
Although not all of the following muscle groups are commonly used, intramuscular injections may be given into the abdominals, biceps, calves, deltoids, gluteals, laterals, pectorals, quadriceps, trapezoids, and triceps.
Alcohol acts as a diuretic. Eight ounces of water is needed to metabolize just 1 ounce of alcohol.