|
|
|
Signs and symptoms of a drug overdose include losing consciousness, fever or sweating, breathing problems, abnormal pulse, and changes in skin color.
Stevens-Johnson syndrome and Toxic Epidermal Necrolysis syndrome are life-threatening reactions that can result in death. Complications include permanent blindness, dry-eye syndrome, lung damage, photophobia, asthma, chronic obstructive pulmonary disease, permanent loss of nail beds, scarring of mucous membranes, arthritis, and chronic fatigue syndrome. Many patients' pores scar shut, causing them to retain heat.
Earwax has antimicrobial properties that reduce the viability of bacteria and fungus in the human ear.
In the ancient and medieval periods, dysentery killed about ? of all babies before they reach 12 months of age. The disease was transferred through contaminated drinking water, because there was no way to adequately dispose of sewage, which contaminated the water.
In 2006, a generic antinausea drug named ondansetron was approved. It is used to stop nausea and vomiting associated with surgery, chemotherapy, and radiation therapy.
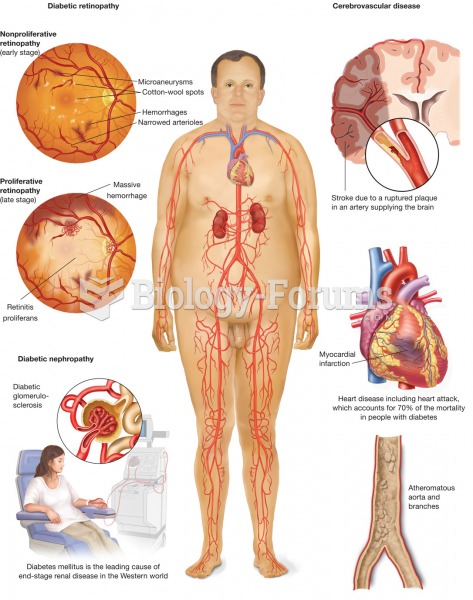 Diabetes mellitus. The metabolic disease diabetes mellitus, with symptoms of polydipsia, polyuria, a
Diabetes mellitus. The metabolic disease diabetes mellitus, with symptoms of polydipsia, polyuria, a
 The gaping hole in the destroyer USS Cole, in the port of Aden, Yemen, was the work of suicide bombe
The gaping hole in the destroyer USS Cole, in the port of Aden, Yemen, was the work of suicide bombe