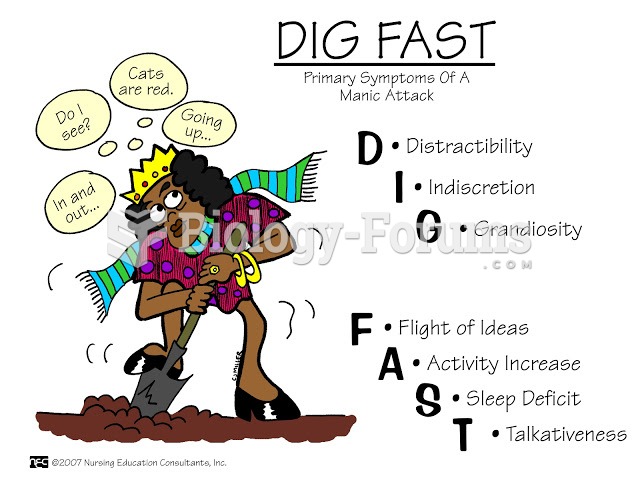
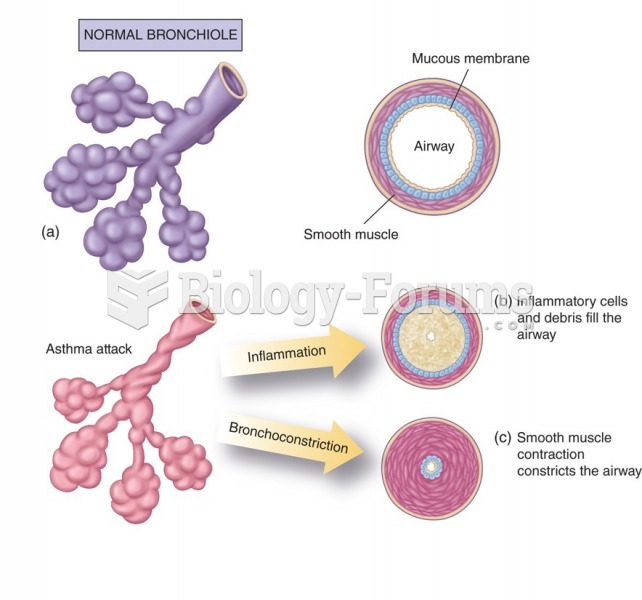
|
|
|
There are immediate benefits of chiropractic adjustments that are visible via magnetic resonance imaging (MRI). It shows that spinal manipulation therapy is effective in decreasing pain and increasing the gaps between the vertebrae, reducing pressure that leads to pain.
There are actually 60 minerals, 16 vitamins, 12 essential amino acids, and three essential fatty acids that your body needs every day.
Cyanide works by making the human body unable to use oxygen.
The Food and Drug Administration has approved Risperdal, an adult antipsychotic drug, for the symptomatic treatment of irritability in children and adolescents with autism. The approval is the first for the use of a drug to treat behaviors associated with autism in children. These behaviors are included under the general heading of irritability and include aggression, deliberate self-injury, and temper tantrums.
Atropine, along with scopolamine and hyoscyamine, is found in the Datura stramonium plant, which gives hallucinogenic effects and is also known as locoweed.
 Enhanced photomicrograph showing a macrophage (purple) attack- ing bacillus Escherichia coli (green)
Enhanced photomicrograph showing a macrophage (purple) attack- ing bacillus Escherichia coli (green)
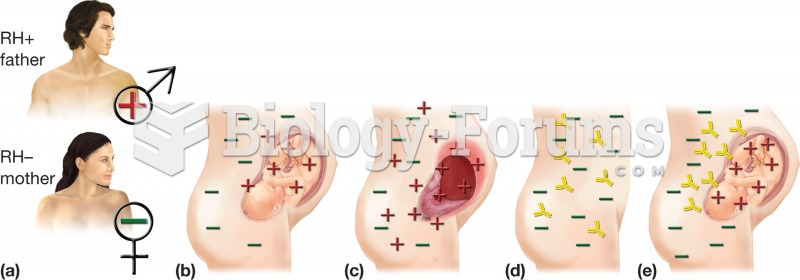 Erythroblastosis fetalis. (a) The condition occurs with an RH+ father and RH– mother. (b) First preg
Erythroblastosis fetalis. (a) The condition occurs with an RH+ father and RH– mother. (b) First preg
 The gaping hole in the destroyer USS Cole, in the port of Aden, Yemen, was the work of suicide bombe
The gaping hole in the destroyer USS Cole, in the port of Aden, Yemen, was the work of suicide bombe