|
|
|
All patients with hyperparathyroidism will develop osteoporosis. The parathyroid glands maintain blood calcium within the normal range. All patients with this disease will continue to lose calcium from their bones every day, and there is no way to prevent the development of osteoporosis as a result.
Most fungi that pathogenically affect humans live in soil. If a person is not healthy, has an open wound, or is immunocompromised, a fungal infection can be very aggressive.
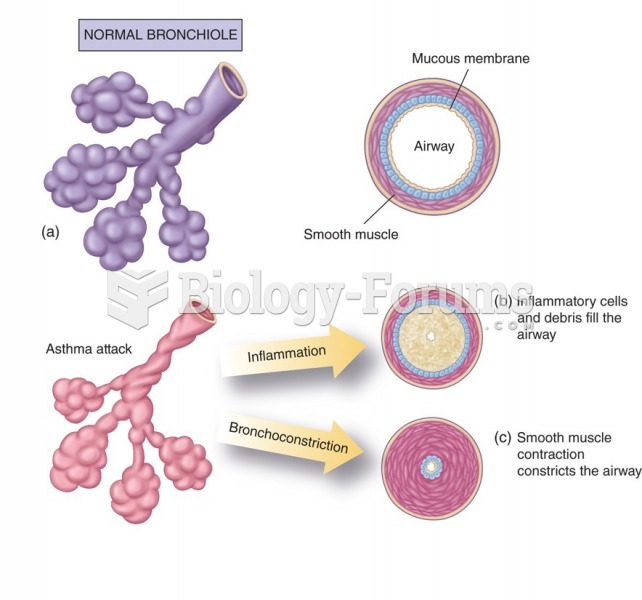
Allergies play a major part in the health of children. The most prevalent childhood allergies are milk, egg, soy, wheat, peanuts, tree nuts, and seafood.
Egg cells are about the size of a grain of sand. They are formed inside of a female's ovaries before she is even born.
People often find it difficult to accept the idea that bacteria can be beneficial and improve health. Lactic acid bacteria are good, and when eaten, these bacteria improve health and increase longevity. These bacteria included in foods such as yogurt.