This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
The most common treatment options for addiction include psychotherapy, support groups, and individual counseling.
Did you know?
The U.S. Preventive Services Task Force recommends that all women age 65 years of age or older should be screened with bone densitometry.
Did you know?
Carbamazepine can interfere with the results of home pregnancy tests. If you are taking carbamazepine, do not try to test for pregnancy at home.
Did you know?
It is difficult to obtain enough calcium without consuming milk or other dairy foods.
Did you know?
The first documented use of surgical anesthesia in the United States was in Connecticut in 1844.
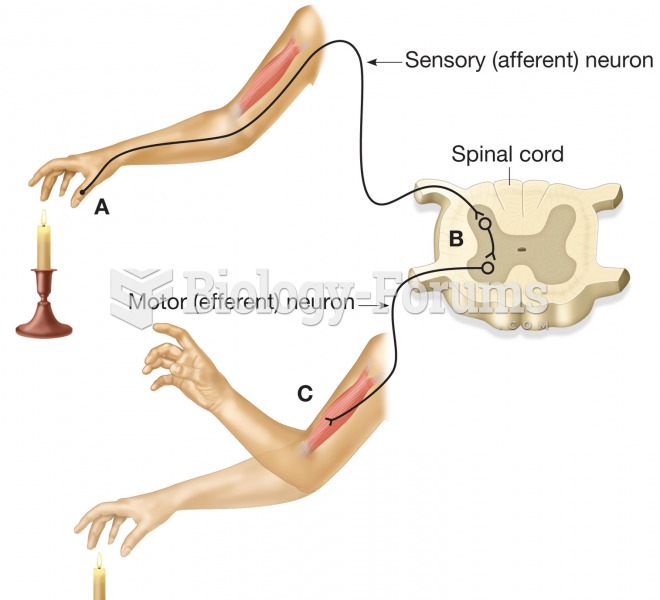 The functional structure of the peripheral nervous system. (A) Afferent or sensory neurons carry sen
The functional structure of the peripheral nervous system. (A) Afferent or sensory neurons carry sen
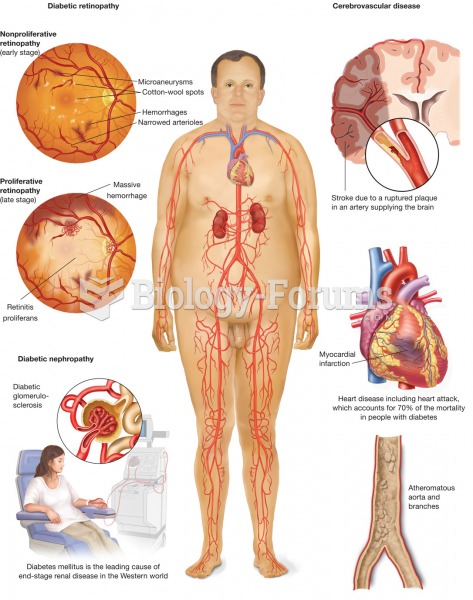 Diabetes mellitus. The metabolic disease diabetes mellitus, with symptoms of polydipsia, polyuria, a
Diabetes mellitus. The metabolic disease diabetes mellitus, with symptoms of polydipsia, polyuria, a