|
|
|
In 2010, opiate painkllers, such as morphine, OxyContin®, and Vicodin®, were tied to almost 60% of drug overdose deaths.
The horizontal fraction bar was introduced by the Arabs.
Eat fiber! A diet high in fiber can help lower cholesterol levels by as much as 10%.
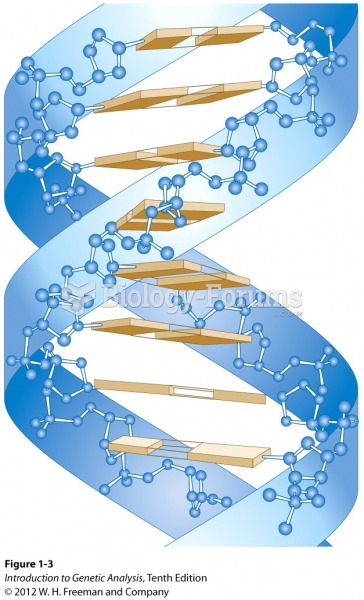
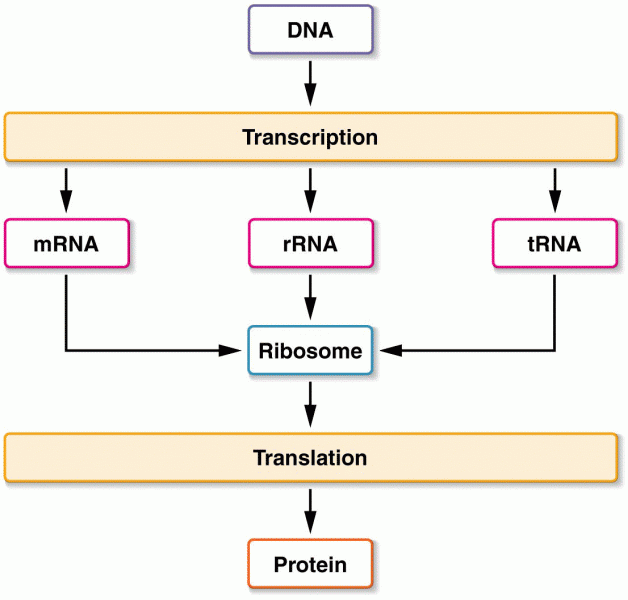
Interferon was scarce and expensive until 1980, when the interferon gene was inserted into bacteria using recombinant DNA technology, allowing for mass cultivation and purification from bacterial cultures.
Asthma-like symptoms were first recorded about 3,500 years ago in Egypt. The first manuscript specifically written about asthma was in the year 1190, describing a condition characterized by sudden breathlessness. The treatments listed in this manuscript include chicken soup, herbs, and sexual abstinence.