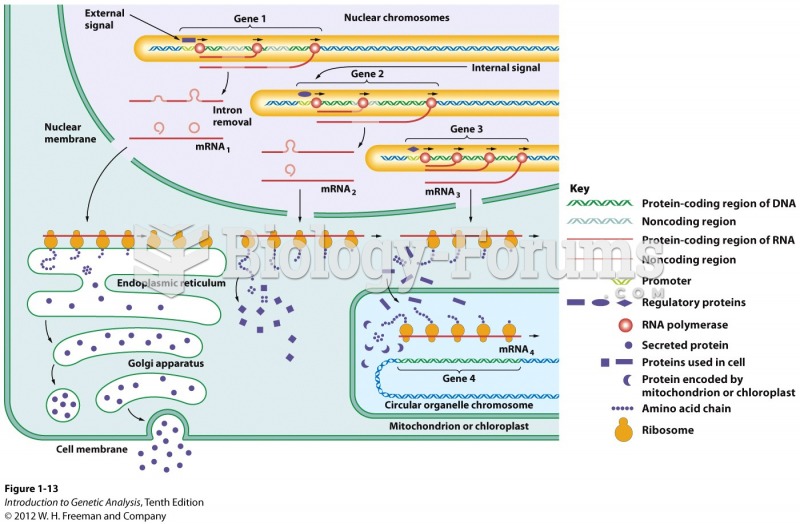
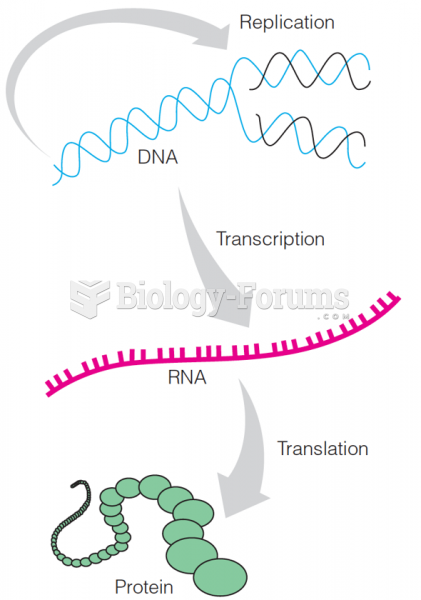
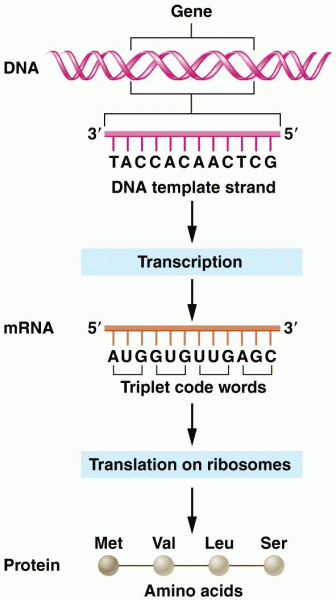
|
|
|
Nearly all drugs pass into human breast milk. How often a drug is taken influences the amount of drug that will pass into the milk. Medications taken 30 to 60 minutes before breastfeeding are likely to be at peak blood levels when the baby is nursing.
Thyroid conditions may make getting pregnant impossible.
Liver spots have nothing whatsoever to do with the liver. They are a type of freckles commonly seen in older adults who have been out in the sun without sufficient sunscreen.
Vaccines prevent between 2.5 and 4 million deaths every year.
According to the American College of Allergy, Asthma & Immunology, more than 50 million Americans have some kind of food allergy. Food allergies affect between 4 and 6% of children, and 4% of adults, according to the CDC. The most common food allergies include shellfish, peanuts, walnuts, fish, eggs, milk, and soy.
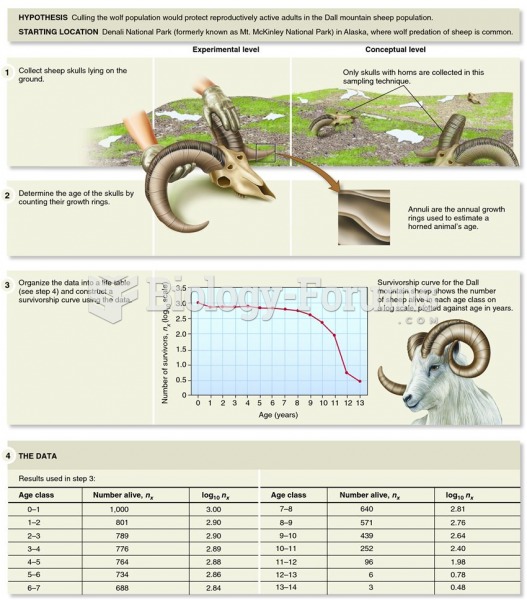 Examining the survivorship curve of a Dall mountain sheep population reveals information on the caus
Examining the survivorship curve of a Dall mountain sheep population reveals information on the caus
 A Bluetooth adapter that plugs into the DLC and transmits global OBD II information to a smart phone ...
A Bluetooth adapter that plugs into the DLC and transmits global OBD II information to a smart phone ...