|
|
|
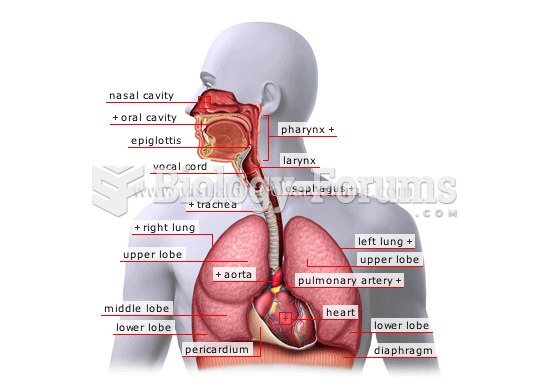
A headache when you wake up in the morning is indicative of sinusitis. Other symptoms of sinusitis can include fever, weakness, tiredness, a cough that may be more severe at night, and a runny nose or nasal congestion.
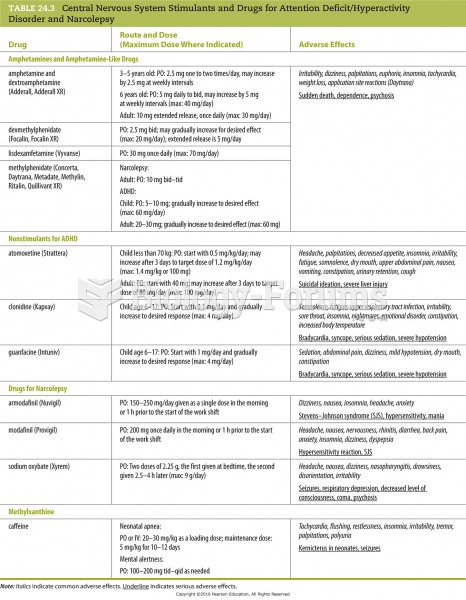
Before a vaccine is licensed in the USA, the Food and Drug Administration (FDA) reviews it for safety and effectiveness. The CDC then reviews all studies again, as well as the American Academy of Pediatrics and the American Academy of Family Physicians. Every lot of vaccine is tested before administration to the public, and the FDA regularly inspects vaccine manufacturers' facilities.
About one in five American adults and teenagers have had a genital herpes infection—and most of them don't know it. People with genital herpes have at least twice the risk of becoming infected with HIV if exposed to it than those people who do not have genital herpes.
Acetaminophen (Tylenol) in overdose can seriously damage the liver. It should never be taken by people who use alcohol heavily; it can result in severe liver damage and even a condition requiring a liver transplant.
Earwax has antimicrobial properties that reduce the viability of bacteria and fungus in the human ear.