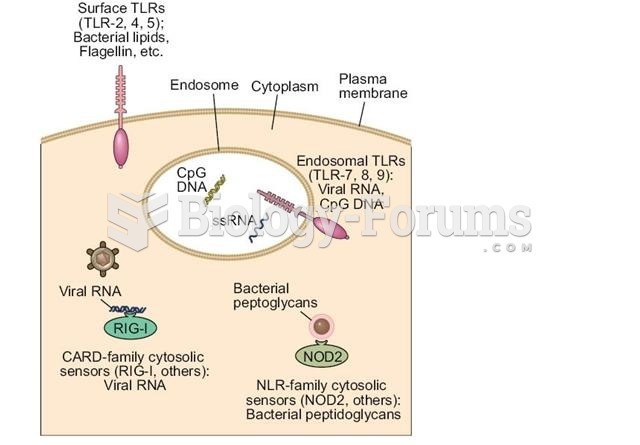
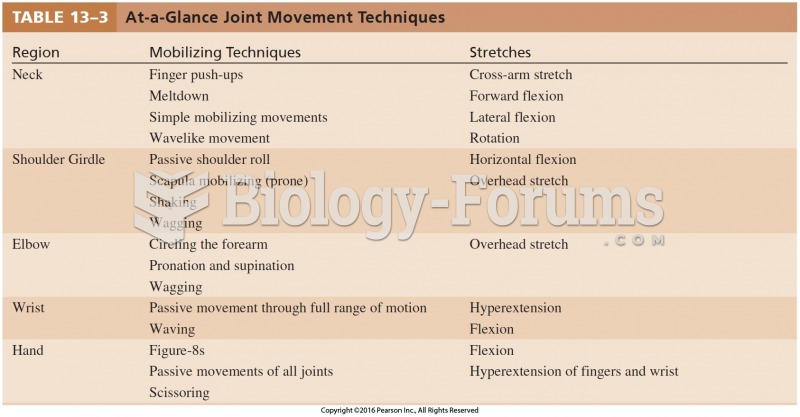
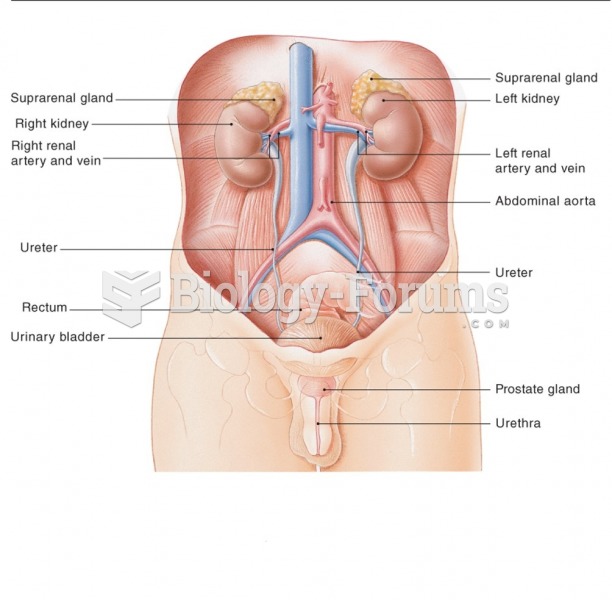
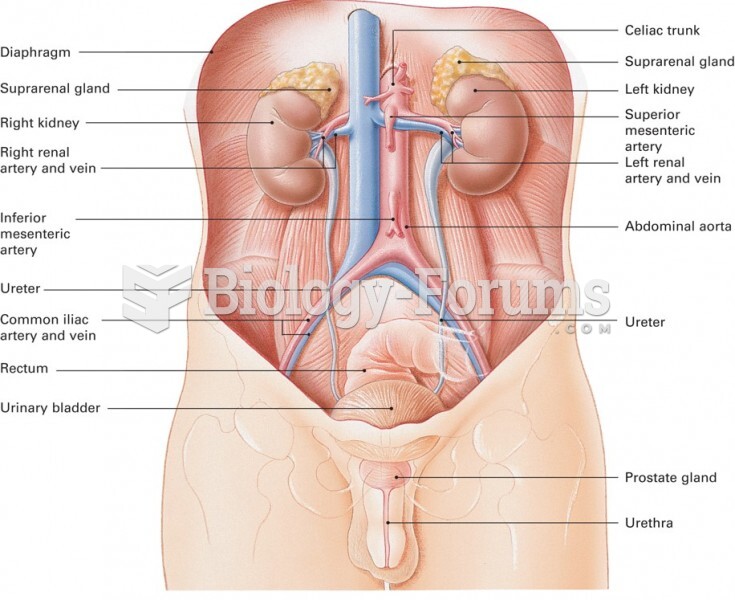
|
|
|
To maintain good kidney function, you should drink at least 3 quarts of water daily. Water dilutes urine and helps prevent concentrations of salts and minerals that can lead to kidney stone formation. Chronic dehydration is a major contributor to the development of kidney stones.
The types of cancer that alpha interferons are used to treat include hairy cell leukemia, melanoma, follicular non-Hodgkin's lymphoma, and AIDS-related Kaposi's sarcoma.
Blood is approximately twice as thick as water because of the cells and other components found in it.
In Eastern Europe and Russia, interferon is administered intranasally in varied doses for the common cold and influenza. It is claimed that this treatment can lower the risk of infection by as much as 60–70%.
The modern decimal position system was the invention of the Hindus (around 800 AD), involving the placing of numerals to indicate their value (units, tens, hundreds, and so on).