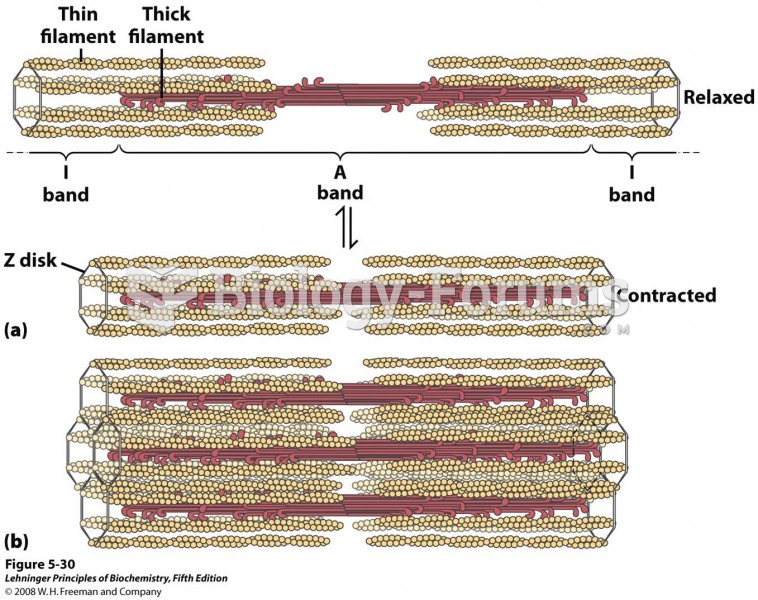
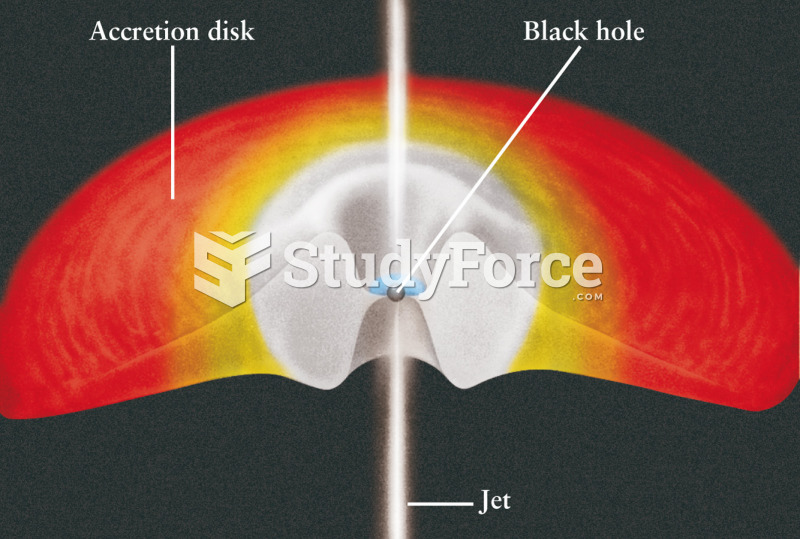
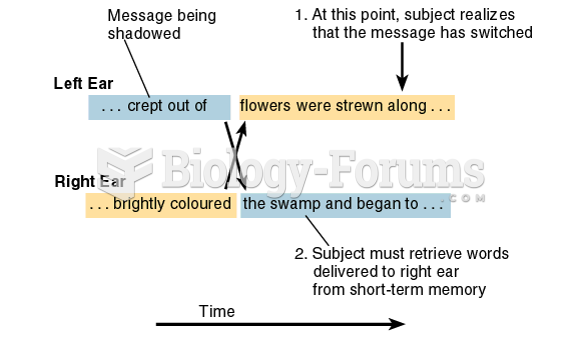
This topic contains a solution. Click here to go to the answer
|
|
|
Did you know?
Many of the drugs used by neuroscientists are derived from toxic plants and venomous animals (such as snakes, spiders, snails, and puffer fish).
Did you know?
In 2012, nearly 24 milliion Americans, aged 12 and older, had abused an illicit drug, according to the National Institute on Drug Abuse (NIDA).
Did you know?
Bacteria have been found alive in a lake buried one half mile under ice in Antarctica.
Did you know?
Certain rare plants containing cyanide include apricot pits and a type of potato called cassava. Fortunately, only chronic or massive ingestion of any of these plants can lead to serious poisoning.
Did you know?
Medication errors are three times higher among children and infants than with adults.
 In the communication technique of collaborating, the nurse sends the message that the nurse and pati
In the communication technique of collaborating, the nurse sends the message that the nurse and pati
 Photograph of the flea that transmits Yersinia pestis to cause bubonic plague, called the oriental r
Photograph of the flea that transmits Yersinia pestis to cause bubonic plague, called the oriental r