|
|
|
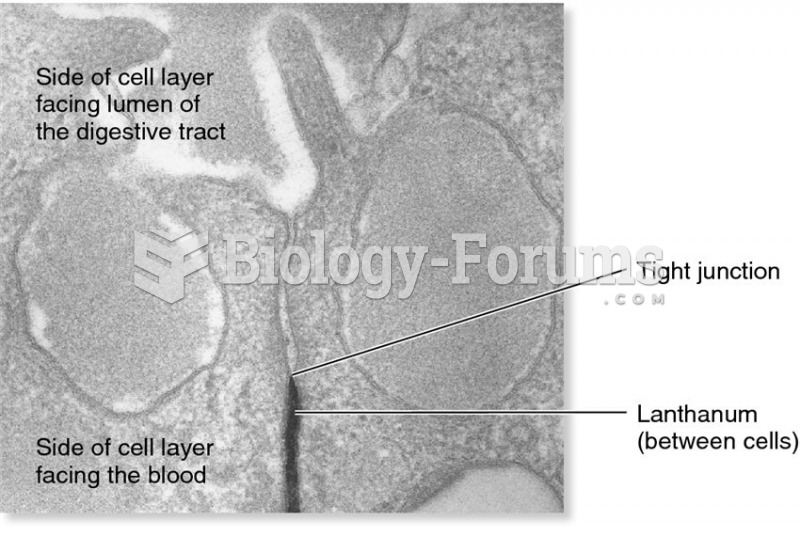
Patients who have been on total parenteral nutrition for more than a few days may need to have foods gradually reintroduced to give the digestive tract time to start working again.
A strange skin disease referred to as Morgellons has occurred in the southern United States and in California. Symptoms include slowly healing sores, joint pain, persistent fatigue, and a sensation of things crawling through the skin. Another symptom is strange-looking, threadlike extrusions coming out of the skin.
Carbamazepine can interfere with the results of home pregnancy tests. If you are taking carbamazepine, do not try to test for pregnancy at home.
Medication errors are more common among seriously ill patients than with those with minor conditions.
In 1885, the Lloyd Manufacturing Company of Albany, New York, promoted and sold "Cocaine Toothache Drops" at 15 cents per bottle! In 1914, the Harrison Narcotic Act brought the sale and distribution of this drug under federal control.