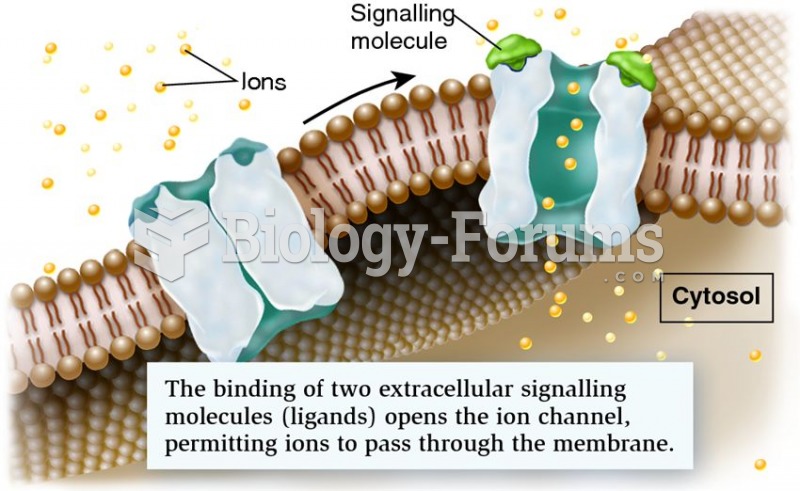
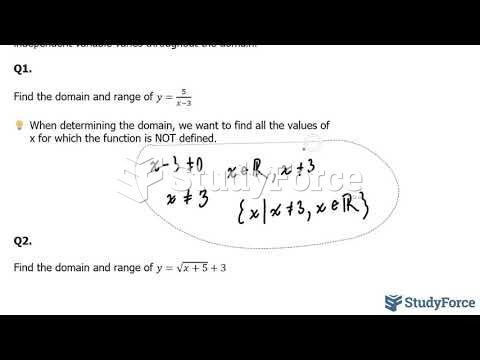
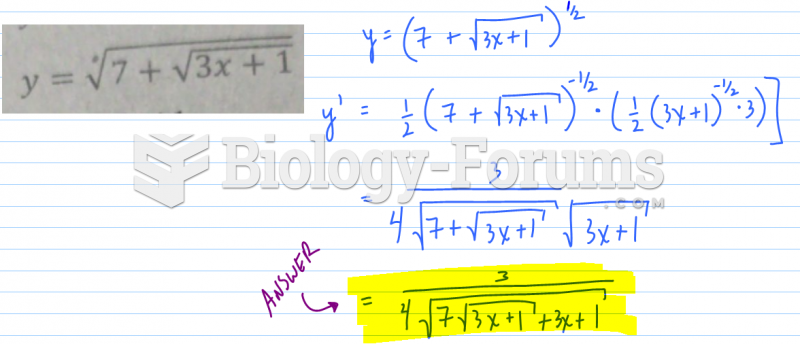
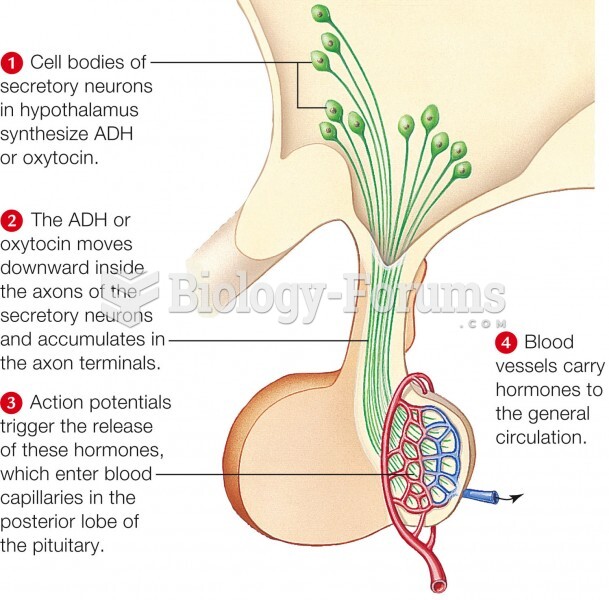
|
|
|
The first monoclonal antibodies were made exclusively from mouse cells. Some are now fully human, which means they are likely to be safer and may be more effective than older monoclonal antibodies.
Throughout history, plants containing cardiac steroids have been used as heart drugs and as poisons (e.g., in arrows used in combat), emetics, and diuretics.
The oldest recorded age was 122. Madame Jeanne Calment was born in France in 1875 and died in 1997. She was a vegetarian and loved olive oil, port wine, and chocolate.
Approximately 25% of all reported medication errors result from some kind of name confusion.
Hypertension is a silent killer because it is deadly and has no significant early symptoms. The danger from hypertension is the extra load on the heart, which can lead to hypertensive heart disease and kidney damage. This occurs without any major symptoms until the high blood pressure becomes extreme. Regular blood pressure checks are an important method of catching hypertension before it can kill you.