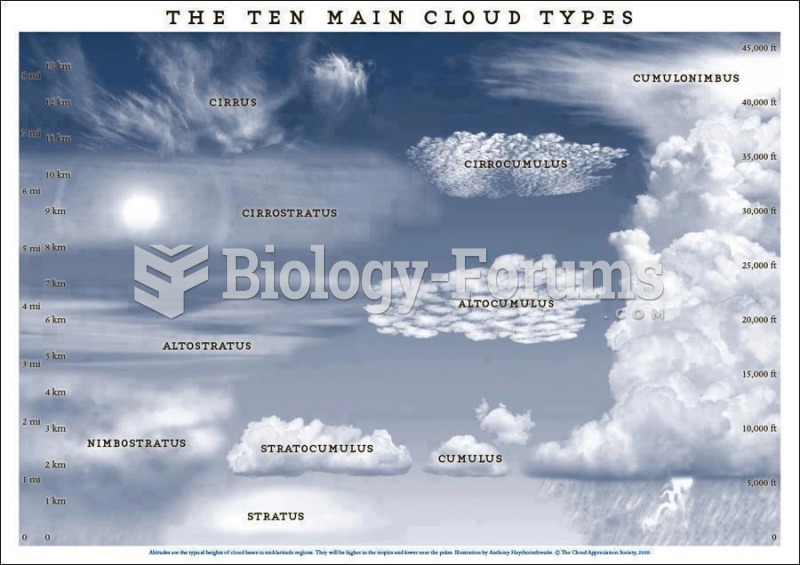
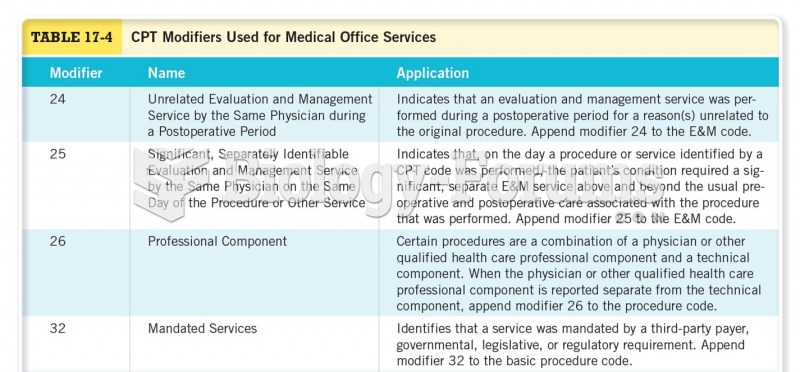
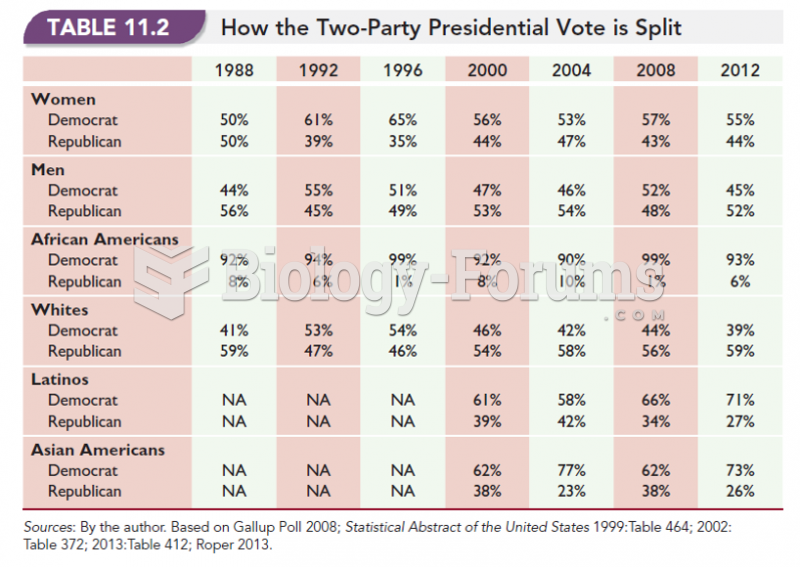
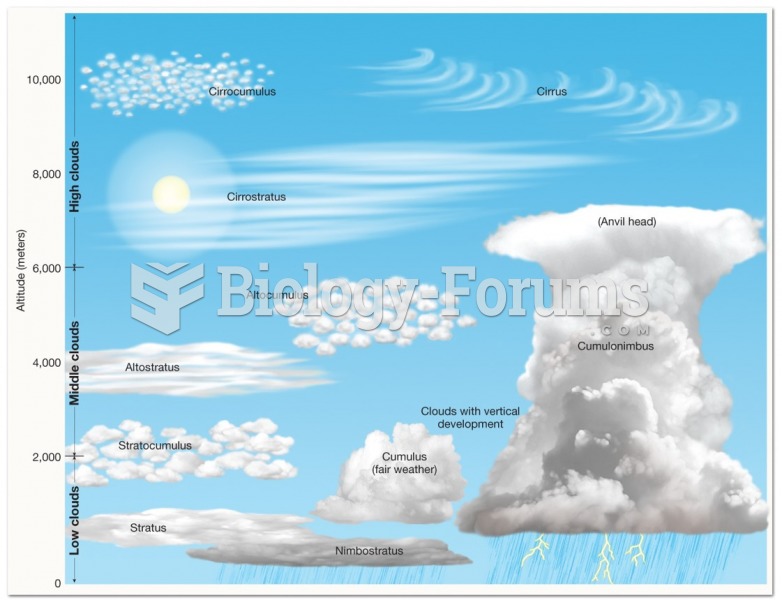
|
|
|
Symptoms of kidney problems include a loss of appetite, back pain (which may be sudden and intense), chills, abdominal pain, fluid retention, nausea, the urge to urinate, vomiting, and fever.
Adult head lice are gray, about ? inch long, and often have a tiny dot on their backs. A female can lay between 50 and 150 eggs within the several weeks that she is alive. They feed on human blood.
Amoebae are the simplest type of protozoans, and are characterized by a feeding and dividing trophozoite stage that moves by temporary extensions called pseudopodia or false feet.
Cyanide works by making the human body unable to use oxygen.
Although the Roman numeral for the number 4 has always been taught to have been "IV," according to historians, the ancient Romans probably used "IIII" most of the time. This is partially backed up by the fact that early grandfather clocks displayed IIII for the number 4 instead of IV. Early clockmakers apparently thought that the IIII balanced out the VIII (used for the number 8) on the clock face and that it just looked better.