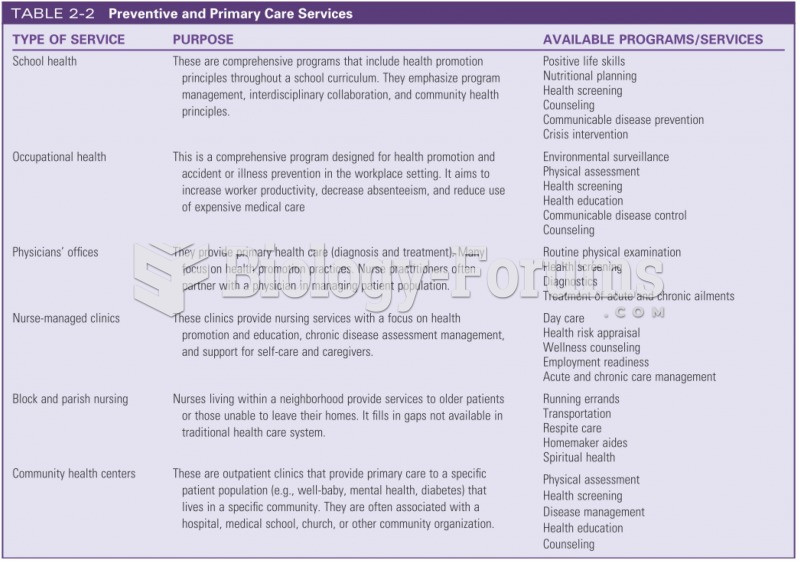
|
|
|
Though “Krazy Glue” or “Super Glue” has the ability to seal small wounds, it is not recommended for this purpose since it contains many substances that should not enter the body through the skin, and may be harmful.
Normal urine is sterile. It contains fluids, salts, and waste products. It is free of bacteria, viruses, and fungi.
Many medications that are used to treat infertility are injected subcutaneously. This is easy to do using the anterior abdomen as the site of injection but avoiding the area directly around the belly button.
About 60% of newborn infants in the United States are jaundiced; that is, they look yellow. Kernicterus is a form of brain damage caused by excessive jaundice. When babies begin to be affected by excessive jaundice and begin to have brain damage, they become excessively lethargic.
A headache when you wake up in the morning is indicative of sinusitis. Other symptoms of sinusitis can include fever, weakness, tiredness, a cough that may be more severe at night, and a runny nose or nasal congestion.