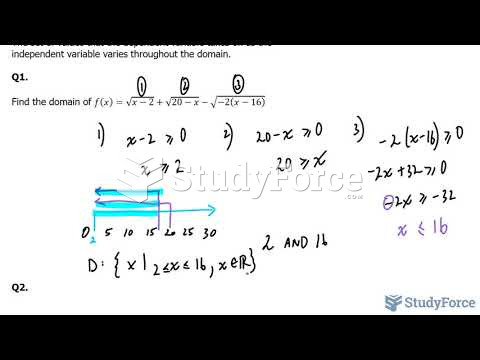
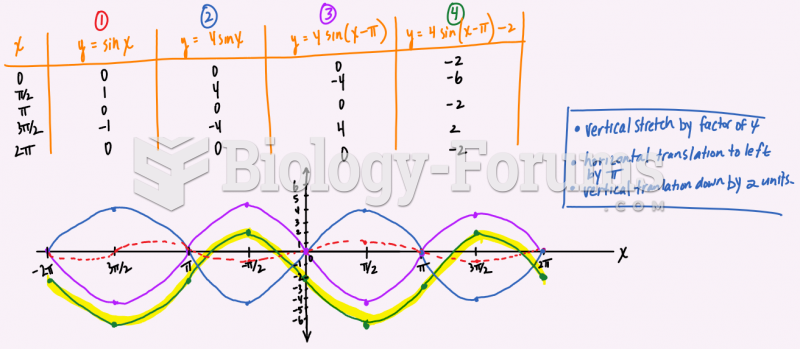
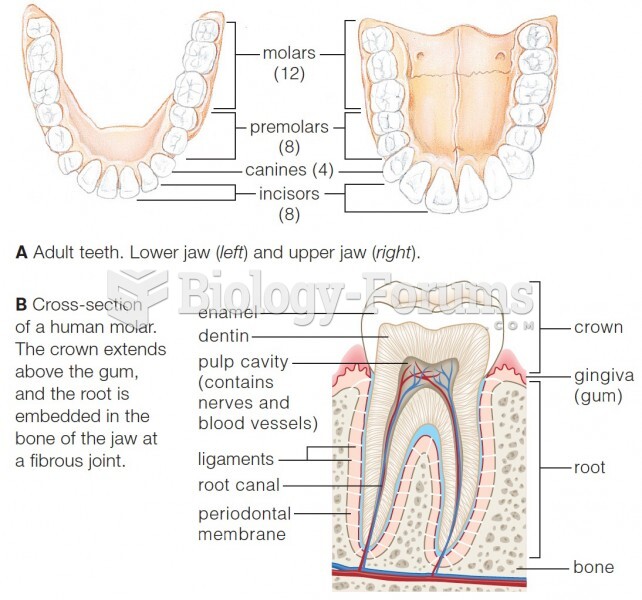
|
|
|
The eye muscles are the most active muscles in the whole body. The external muscles that move the eyes are the strongest muscles in the human body for the job they have to do. They are 100 times more powerful than they need to be.
Asthma occurs in one in 11 children and in one in 12 adults. African Americans and Latinos have a higher risk for developing asthma than other groups.
The National Institutes of Health have supported research into acupuncture. This has shown that acupuncture significantly reduced pain associated with osteoarthritis of the knee, when used as a complement to conventional therapies.
There are over 65,000 known species of protozoa. About 10,000 species are parasitic.
There are major differences in the metabolism of morphine and the illegal drug heroin. Morphine mostly produces its CNS effects through m-receptors, and at k- and d-receptors. Heroin has a slight affinity for opiate receptors. Most of its actions are due to metabolism to active metabolites (6-acetylmorphine, morphine, and morphine-6-glucuronide).