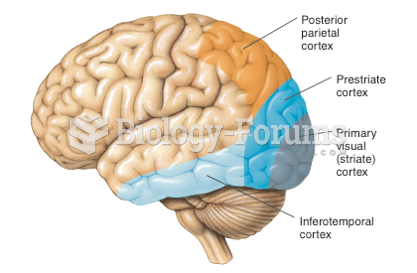
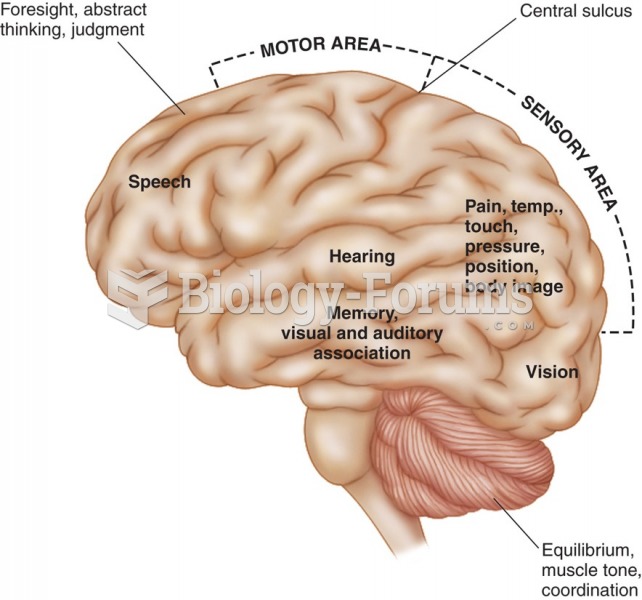
|
|
|
More than 50% of American adults have oral herpes, which is commonly known as "cold sores" or "fever blisters." The herpes virus can be active on the skin surface without showing any signs or causing any symptoms.
In 1886, William Bates reported on the discovery of a substance produced by the adrenal gland that turned out to be epinephrine (adrenaline). In 1904, this drug was first artificially synthesized by Friedrich Stolz.
Approximately one in four people diagnosed with diabetes will develop foot problems. Of these, about one-third will require lower extremity amputation.
Allergies play a major part in the health of children. The most prevalent childhood allergies are milk, egg, soy, wheat, peanuts, tree nuts, and seafood.
The average adult has about 21 square feet of skin.