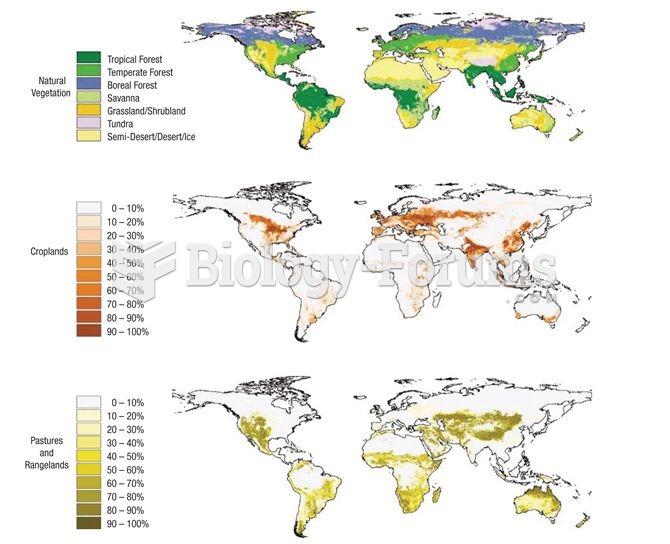
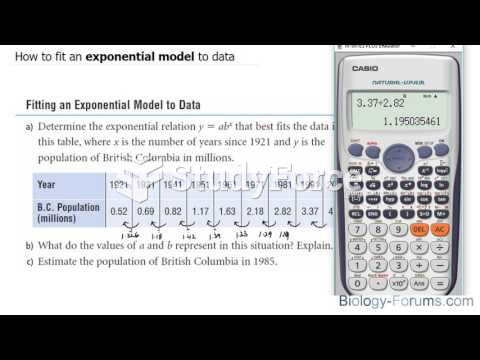
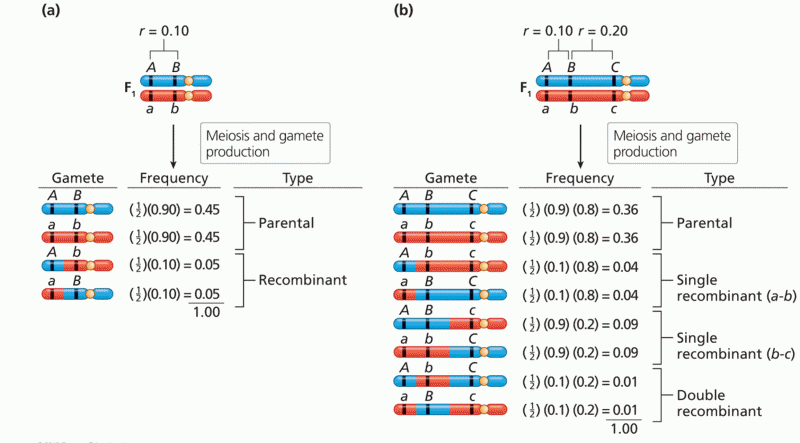
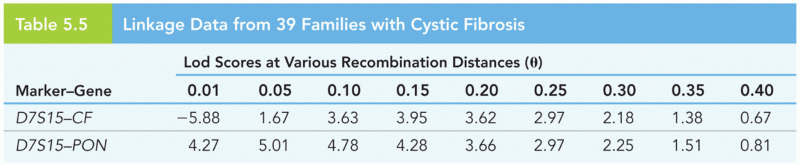
|
|
|
Did you know?
To maintain good kidney function, you should drink at least 3 quarts of water daily. Water dilutes urine and helps prevent concentrations of salts and minerals that can lead to kidney stone formation. Chronic dehydration is a major contributor to the development of kidney stones.
Did you know?
Cucumber slices relieve headaches by tightening blood vessels, reducing blood flow to the area, and relieving pressure.
Did you know?
The most destructive flu epidemic of all times in recorded history occurred in 1918, with approximately 20 million deaths worldwide.
Did you know?
Medication errors are more common among seriously ill patients than with those with minor conditions.
Did you know?
When blood is exposed to air, it clots. Heparin allows the blood to come in direct contact with air without clotting.