|
|
|
People often find it difficult to accept the idea that bacteria can be beneficial and improve health. Lactic acid bacteria are good, and when eaten, these bacteria improve health and increase longevity. These bacteria included in foods such as yogurt.
The liver is the only organ that has the ability to regenerate itself after certain types of damage. As much as 25% of the liver can be removed, and it will still regenerate back to its original shape and size. However, the liver cannot regenerate after severe damage caused by alcohol.
Malaria mortality rates are falling. Increased malaria prevention and control measures have greatly improved these rates. Since 2000, malaria mortality rates have fallen globally by 60% among all age groups, and by 65% among children under age 5.
Urine turns bright yellow if larger than normal amounts of certain substances are consumed; one of these substances is asparagus.
Oxytocin is recommended only for pregnancies that have a medical reason for inducing labor (such as eclampsia) and is not recommended for elective procedures or for making the birthing process more convenient.
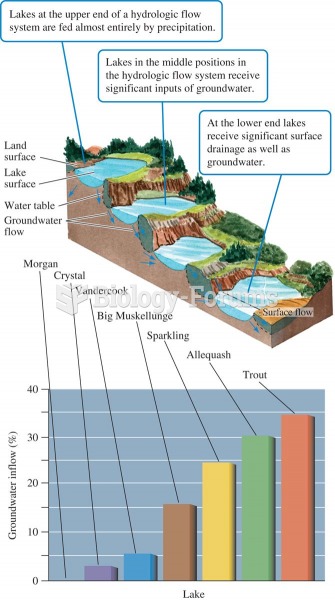 Lake position in the landscape and proportion of water received as groundwater (data from Webster et
Lake position in the landscape and proportion of water received as groundwater (data from Webster et
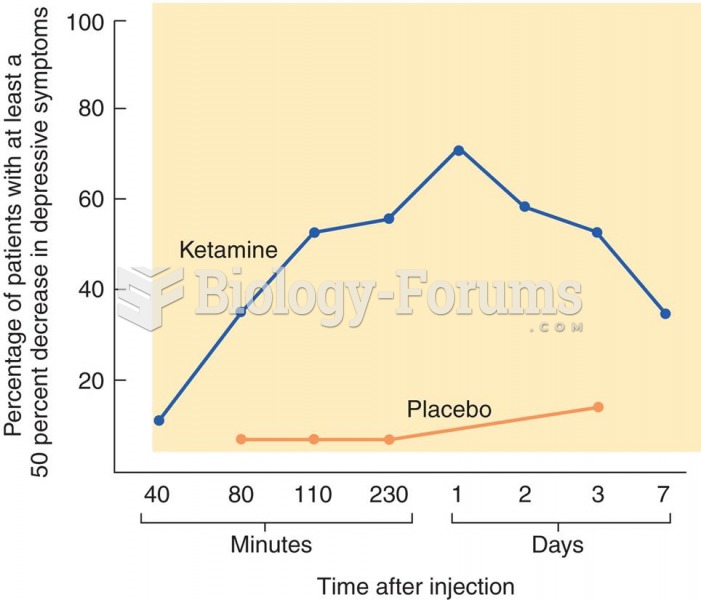 Treatment of Depression with Ketamine The graph shows the effects of ketamine on symptoms of depress
Treatment of Depression with Ketamine The graph shows the effects of ketamine on symptoms of depress