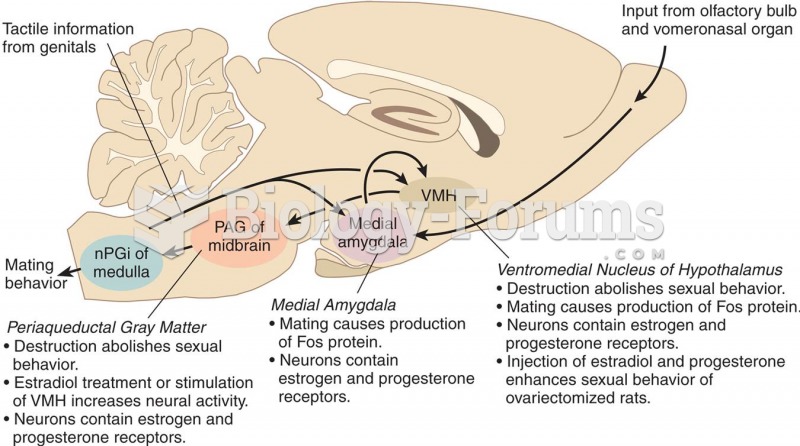
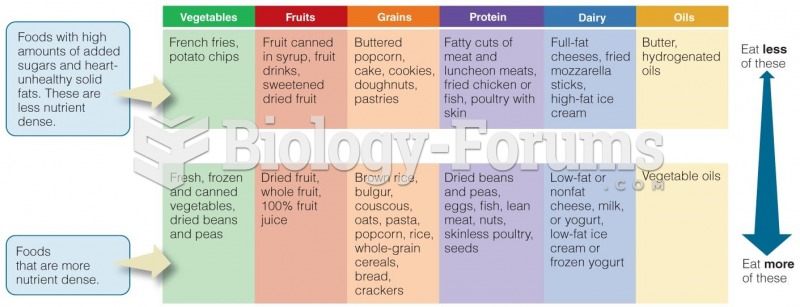
|
|
|
The U.S. Pharmacopeia Medication Errors Reporting Program states that approximately 50% of all medication errors involve insulin.
Amoebae are the simplest type of protozoans, and are characterized by a feeding and dividing trophozoite stage that moves by temporary extensions called pseudopodia or false feet.
Individuals are never “cured” of addictions. Instead, they learn how to manage their disease to lead healthy, balanced lives.
Asthma attacks and symptoms usually get started by specific triggers (such as viruses, allergies, gases, and air particles). You should talk to your doctor about these triggers and find ways to avoid or get rid of them.
Eating food that has been cooked with poppy seeds may cause you to fail a drug screening test, because the seeds contain enough opiate alkaloids to register as a positive.
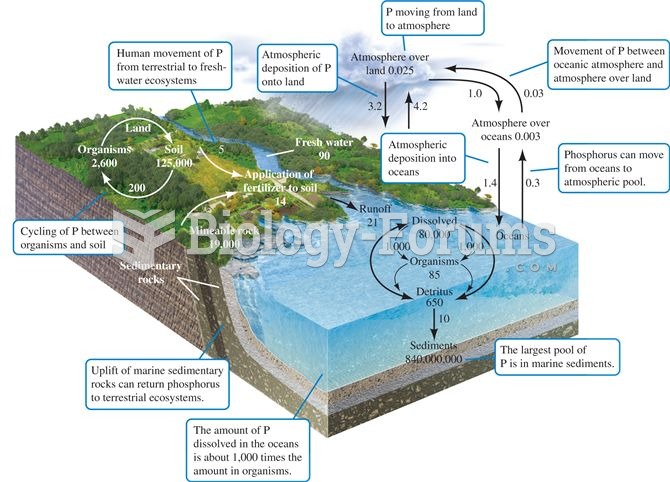 The phosphorus cycle. Numbers are 1012 g P or fluxes as 1012 g P per year (data from Schlesinger 199
The phosphorus cycle. Numbers are 1012 g P or fluxes as 1012 g P per year (data from Schlesinger 199
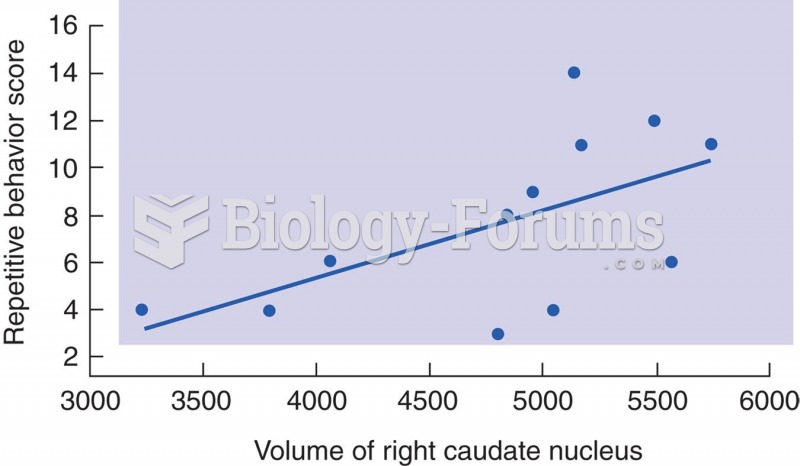
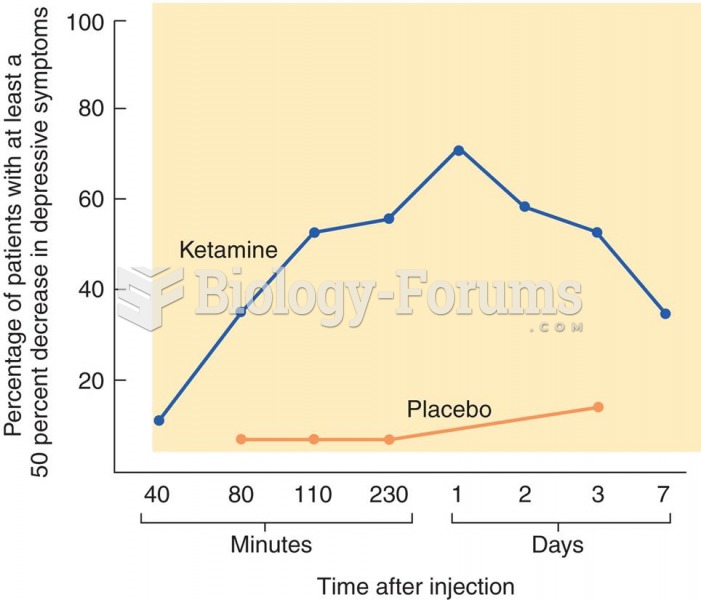 Treatment of Depression with Ketamine The graph shows the effects of ketamine on symptoms of depress
Treatment of Depression with Ketamine The graph shows the effects of ketamine on symptoms of depress