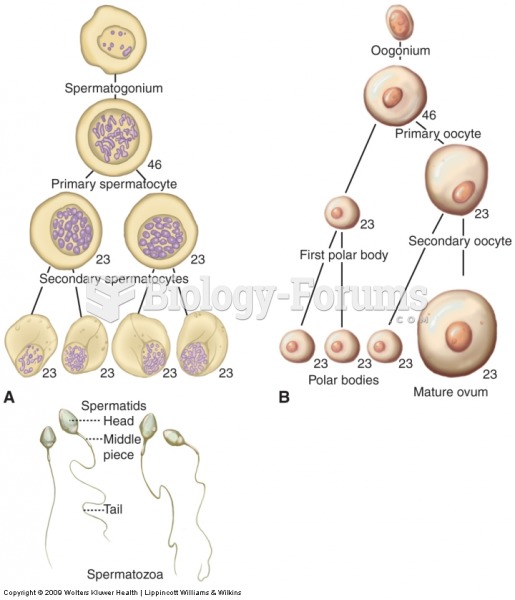
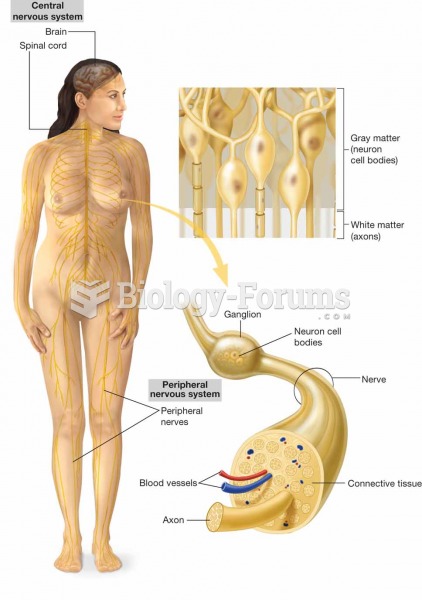
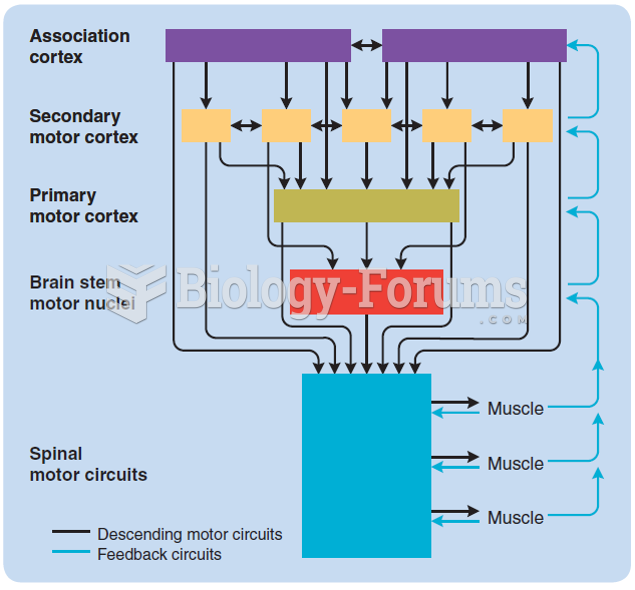
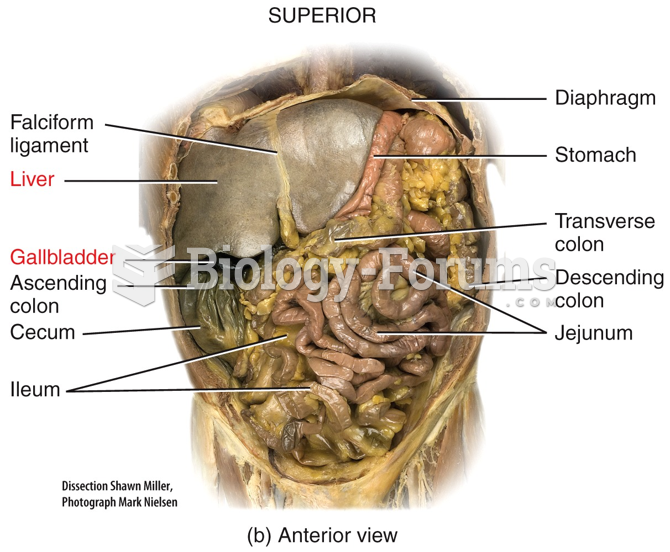
|
|
|
On average, someone in the United States has a stroke about every 40 seconds. This is about 795,000 people per year.
A seasonal flu vaccine is the best way to reduce the chances you will get seasonal influenza and spread it to others.
Patients should never assume they are being given the appropriate drugs. They should make sure they know which drugs are being prescribed, and always double-check that the drugs received match the prescription.
Vaccines cause herd immunity. If the majority of people in a community have been vaccinated against a disease, an unvaccinated person is less likely to get the disease since others are less likely to become sick from it and spread the disease.
When blood is exposed to air, it clots. Heparin allows the blood to come in direct contact with air without clotting.