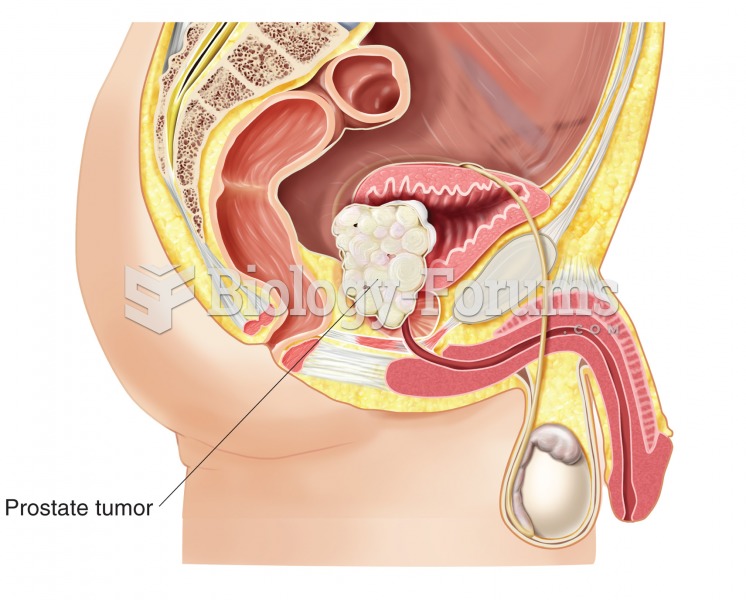
|
|
|
It is believed that humans initially contracted crabs from gorillas about 3 million years ago from either sleeping in gorilla nests or eating the apes.
Eating carrots will improve your eyesight. Carrots are high in vitamin A (retinol), which is essential for good vision. It can also be found in milk, cheese, egg yolks, and liver.
Liver spots have nothing whatsoever to do with the liver. They are a type of freckles commonly seen in older adults who have been out in the sun without sufficient sunscreen.
In 1835 it was discovered that a disease of silkworms known as muscardine could be transferred from one silkworm to another, and was caused by a fungus.
In 2010, opiate painkllers, such as morphine, OxyContin®, and Vicodin®, were tied to almost 60% of drug overdose deaths.