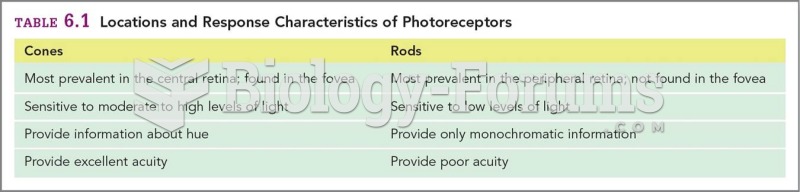
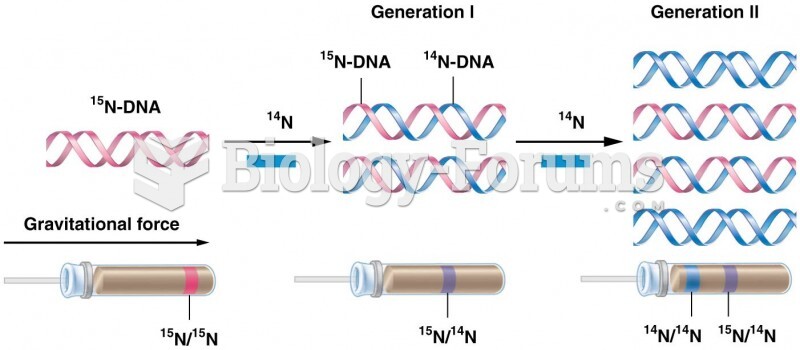
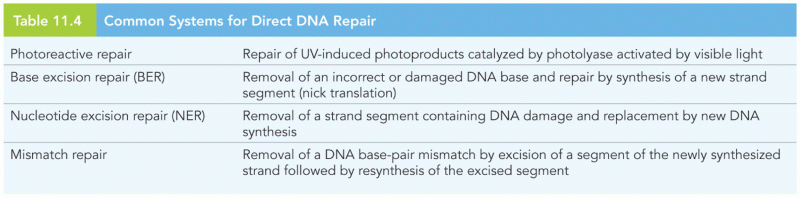
|
|
|
The newest statin drug, rosuvastatin, has been called a superstatin because it appears to reduce LDL cholesterol to a greater degree than the other approved statin drugs.
Pregnant women usually experience a heightened sense of smell beginning late in the first trimester. Some experts call this the body's way of protecting a pregnant woman from foods that are unsafe for the fetus.
Your heart beats over 36 million times a year.
To maintain good kidney function, you should drink at least 3 quarts of water daily. Water dilutes urine and helps prevent concentrations of salts and minerals that can lead to kidney stone formation. Chronic dehydration is a major contributor to the development of kidney stones.
Chronic necrotizing aspergillosis has a slowly progressive process that, unlike invasive aspergillosis, does not spread to other organ systems or the blood vessels. It most often affects middle-aged and elderly individuals, spreading to surrounding tissue in the lungs. The disease often does not respond to conventionally successful treatments, and requires individualized therapies in order to keep it from becoming life-threatening.