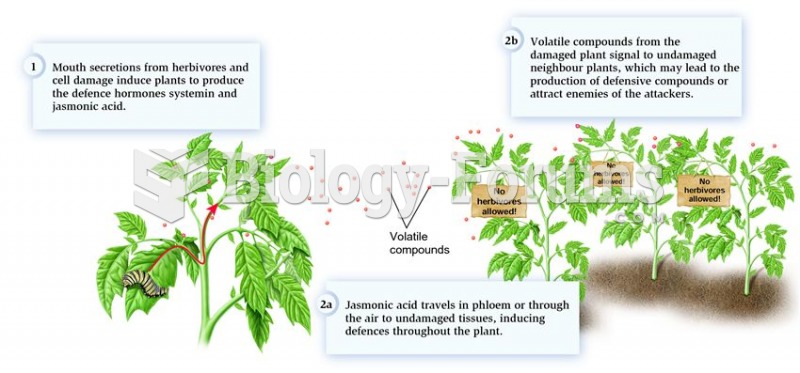
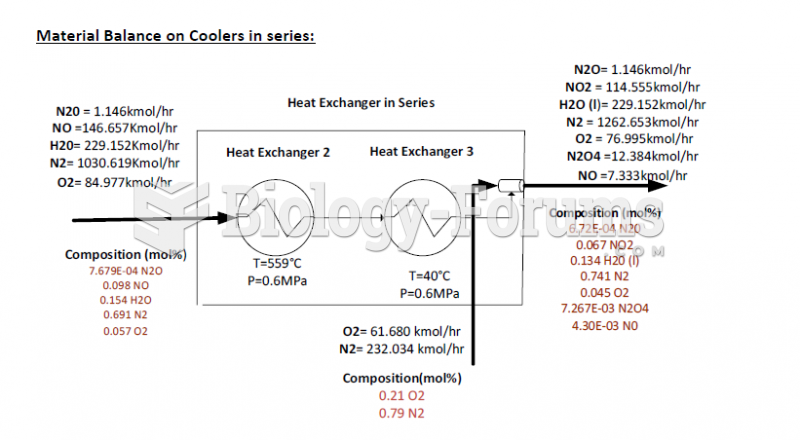
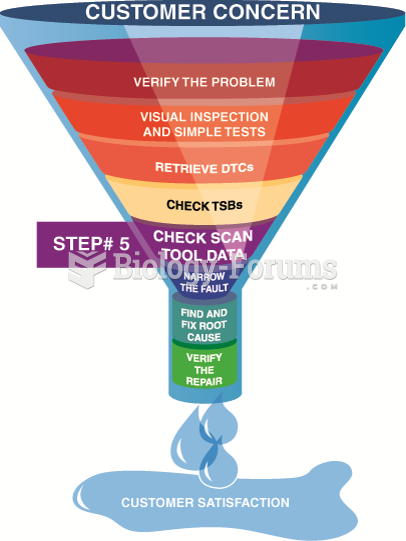
|
|
|
Astigmatism is the most common vision problem. It may accompany nearsightedness or farsightedness. It is usually caused by an irregularly shaped cornea, but sometimes it is the result of an irregularly shaped lens. Either type can be corrected by eyeglasses, contact lenses, or refractive surgery.
In most climates, 8 to 10 glasses of water per day is recommended for adults. The best indicator for adequate fluid intake is frequent, clear urination.
The use of salicylates dates back 2,500 years to Hippocrates's recommendation of willow bark (from which a salicylate is derived) as an aid to the pains of childbirth. However, overdosage of salicylates can harm body fluids, electrolytes, the CNS, the GI tract, the ears, the lungs, the blood, the liver, and the kidneys and cause coma or death.
Pope Sylvester II tried to introduce Arabic numbers into Europe between the years 999 and 1003, but their use did not catch on for a few more centuries, and Roman numerals continued to be the primary number system.
It is important to read food labels and choose foods with low cholesterol and saturated trans fat. You should limit saturated fat to no higher than 6% of daily calories.